Author: Stephen Katte, CoinTelegraph; Translator: Baishui, Golden Finance
Blockchain investigator ZachXBT said he had uncovered evidence of a sophisticated network of North Korean developers who were earning up to $500,000 a month working for “mature” crypto projects. ”
ZachXBT told his 618,000 followers in an Aug. 15 X post that he believes a “single entity in Asia,” possibly operating from North Korea, is making $300,000 to $500,000 a month and employing at least 21 people working on more than 25 crypto projects.
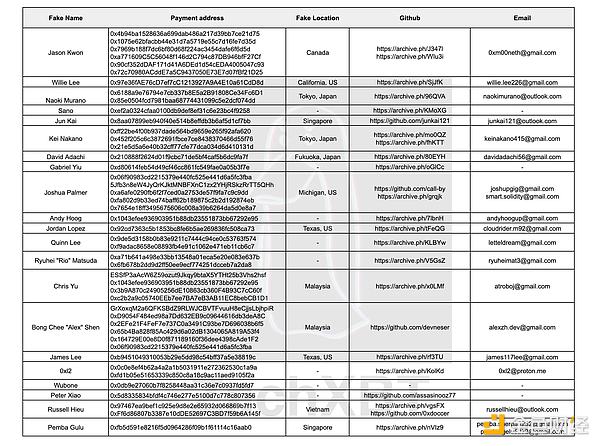
Blockchain researcher ZachXBT claims to have found 21 "Recently, a team came to me for help after $1.3 million was stolen from the national treasury after malicious code was pushed," ZachXBT said.
"Unbeknownst to the team, they had hired multiple North Korean IT workers using fake identities as developers. ”
ZachXBT claims that the $1.3 million recently stolen by North Korean workers was laundered through a series of transactions, including transfers to the stolen addresses and finally the transfer of 16.5 Ethereum to two different exchanges.
After further investigation into these developers, ZachXBT believes they are part of a wider network.
By tracking multiple payment addresses, he found that a group of developers "received $375,000 last month" in previous transactions totaling $5.5 million, which flowed into an exchange deposit address sometime between July 2023 and 2024.
These payments were subsequently linked to North Korean IT worker and individual Sim Hyon Sop, who is sanctioned by the Office of Foreign Assets Control (OFAC) for allegedly coordinating fund transfers that were ultimately used to support North Korea's weapons programs.
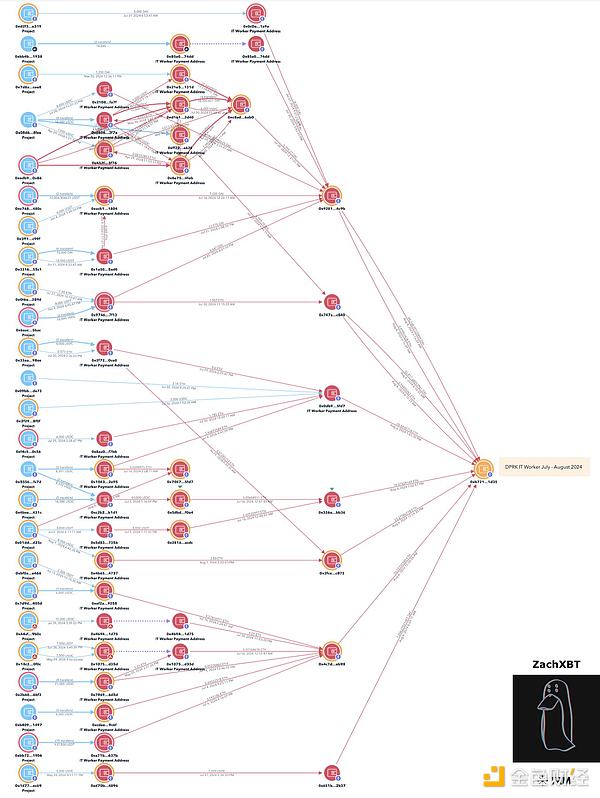
ZachXBT believes a group of North Korean developers using fake identities received $375,000 in the past month. Source: ZachXBT
ZachXBT said his investigation found other payment addresses were closely tied to another OFAC-sanctioned individual, Sang Man Kim, who has been linked to North Korea-related cybercrime in the past.
U.S. law enforcement believes Kim was "involved in paying salaries to family members of the Chinyong Overseas North Korean Workers Delegation" and received $200,000 for selling IT equipment to North Korean-affiliated groups in China and Russia.
ZachXBT also found overlap in Russian telecom IPs between developers claiming to work in the U.S. and Malaysia. At least one worker “accidentally revealed their other identities on a notepad.”
Some of the developers he found were even placed by recruiting firms, and in some cases, they referred each other for jobs.
“Many experienced teams hired these developers, so it’s unfair to single them out,” ZachXBT said.
“Soon after posting another project, I discovered that they had hired a North Korean IT worker listed in my list (Naoki Murano) and shared my post in their chat. Within two minutes, Naoki had left the chat and cleared his GitHub.”
Groups linked to North Korea are believed to be behind multiple cyberattacks and other scams over the years. Their cybercrime tactics often involve phishing, exploiting software vulnerabilities, network intrusions, private key vulnerabilities, and face-to-face penetration. Some are also known to do these jobs to earn a salary, which is then sent back to the country.
In 2022, the U.S. Departments of Justice, State, and Treasury issued a joint advisory warning of the influx of North Korean workers into various freelance technology jobs, especially in cryptocurrency.
The most notorious group associated with the Hermit Kingdom, the Lazarus Group, is said to have stolen more than $3 billion in crypto assets over a six-year period ending in 2023.
 Weiliang
Weiliang






