Article source: Elliptic; Compiled by: Jinse Finance xiaozou
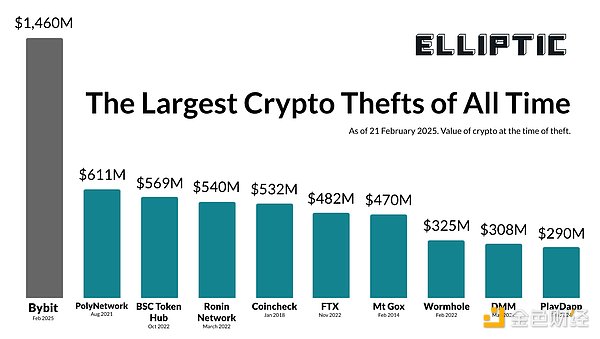
On February 21, 2025, Dubai-based cryptocurrency exchange Bybit suffered a theft of approximately $1.46 billion in crypto assets. Preliminary reports indicate that the attackers used malware to trick the exchange into approving transactions that transferred funds to the thieves' accounts.
This is the largest cryptocurrency theft to date, far exceeding the $611 million stolen from Poly Network in 2021 (and most of the funds in that case were eventually returned by hackers). In fact, this is almost certainly the largest single theft in history, with the previous record holder being Saddam Hussein, who stole $1 billion from the Central Bank of Iraq on the eve of the Iraq War in 2003.
Elliptic analyzed a variety of factors, including the analysis of the money laundering path of the stolen crypto assets, and determined that the mastermind behind the Bybit theft was North Korea's Lazarus Group. Since 2017, hackers associated with North Korea have stolen more than $6 billion in crypto assets, which are allegedly used for the country's ballistic missile program.
The Lazarus Group has developed powerful and sophisticated attack capabilities that can not only invade target organizations to steal crypto assets, but also launder stolen funds through thousands of blockchain transactions. After the theft, Elliptic worked around the clock with Bybit, cryptocurrency service providers and other investigators to track the stolen funds and prevent them from being realized. As a leading global provider of crypto asset exchange and wallet screening solutions, Elliptic's software is alerting customers around the world to ask if they have received any stolen funds from the theft. This has directly led to the freezing of some of the funds stolen from Bybit.
The money laundering process of the Lazarus Group usually follows a typical pattern. The first step is to exchange all the stolen tokens for "native" blockchain assets, such as ETH. This is because tokens have issuers who can "freeze" wallets containing stolen assets in certain circumstances, while there is no central authority that can freeze ETH or Bitcoin.
This is exactly what happened in the minutes after the Bybit theft, with hundreds of millions of dollars of stolen tokens such as stETH and cmETH being exchanged for ETH. The attackers used decentralized exchanges (DEXs) to accomplish this, likely to avoid asset freezes that might be encountered when using centralized exchanges to launder funds.
The second step in the money laundering process is to “layer” the stolen funds in an attempt to obscure the transaction path. The transparent nature of blockchains means that these transaction paths can be traced, but these layering strategies complicate the tracing process and buy valuable time for money launderers to cash out. The layering process can take many forms, including:
Moving funds through a large number of cryptocurrency wallets
Using cross-chain bridges or exchanges to move funds to other blockchains
Using DEXs, token swap services, or exchanges to switch between different crypto assets
Using “mixers” such as Tornado Cash or Cryptomixer
The Lazarus Group is currently in the second stage of laundering its funds. Within two hours of the theft, the stolen funds were sent to 50 different wallets, each holding approximately 10,000 ETH. These wallets are being systematically emptied - as of 10 PM UTC on February 23, 10% of the stolen assets, now worth $140 million, had been moved from these wallets.
Once the funds are moved from these wallets, they are laundered through a variety of services, including DEXs, cross-chain bridges, and centralized exchanges. However, one cryptocurrency exchange called eXch has emerged as a major willing facilitator of this money laundering. eXch is known for allowing users to anonymously exchange crypto assets, which has led to it being used to exchange hundreds of millions of dollars in crypto assets from criminal activity, including multiple thefts perpetrated by North Korea. Since the hack, tens of millions of dollars worth of Bybit’s stolen crypto assets have been exchanged through eXch. Despite direct requests from Bybit, eXch has refused to stop this activity.
The stolen ETH is being gradually converted to Bitcoin through eXch and other services. If past money laundering patterns are followed, we may see the use of mixers to further obfuscate transaction paths. However, this may be challenging due to the sheer size of the stolen funds.
North Korea’s Lazarus Group is the most professional and resourceful crypto money launderer in existence, constantly adapting its techniques to evade identification and seizure of stolen assets. Since the minutes following the Bybit theft, the Elliptic team has been working around the clock with Bybit, clients, and other investigators to track these funds and prevent the North Korean regime from benefiting from them.
 Catherine
Catherine







