PayPal Gets Approval For Crypto Services In UK
The company is only the fourth entity that has been approved to offer crypto services to UK customers.
 Clement
Clement
Author: Teng Yan & 0xAce; Translator: Jinse Finance xiaozou
In the field of artificial intelligence, privacy is no longer an option - it is a matter of life and death.
Nillion is a decentralized infrastructure designed for managing privacy-sensitive data for applications such as AI and private DeFi. The team has partnered with Virtuals, NEAR, Aptos, Arbitrum, etc. The Nillion ecosystem is on the rise, let's explore it in depth in this article.
Abstract of this article:
Nillion is redefining privacy-preserving computing - a key missing link in the next generation of AI.
Privacy is no longer an option. AI agents need access to sensitive data to function, but today’s infrastructure forces users to choose between privacy and practicality.
Blind computation changes this. Nillion enables computation on encrypted data without exposing it, solving the trust problem for AI.
The Nillion network architecture consists of two key components, each with a unique and important role: the coordination layer (nilChain) and Petnet (Privacy Enhanced Technology Network).
Multi-layered privacy protection. Rather than relying on a single approach, Nillion seamlessly integrates MPC, FHE, ZKP, and TEE into a privacy protection stack.
Backed by a strong team (including Uber’s founding engineers and cryptography veterans) and strong financial backing, it has raised $50 million from top investors.
NIL's token economics are designed to drive adoption. NIL will power the network, ensuring operational security while driving burn-based demand as usage scales.
For decades, we've dreamed of truly having personal AI assistants.
From Iron Man's JARVIS managing every aspect of Tony Stark's life (and occasionally saving him), to Star Trek's computer knowing exactly how hot Picard likes his tea (it's always hot), to Samantha in Her - who not only organizes Theodore's inbox, but also philosophizes about existential questions while falling in love.

They reflect a common truth: Being human is exhausting.
JARVIS doesn't just operate Tony Stark's suit. He also schedules meetings, orders groceries, pays bills, and might suggest that a 3 a.m. meeting isn't a good idea for good health.
When we see these, we think: Yes, that's it. I need this.
We keep inventing these fictional assistants because, deep down, we all long for someone — or something — that can ease the relentless mental burden of modern life.
An assistant that can remember things we’ve forgotten, spot patterns we’ve overlooked, and maybe even stop us from sending that 2 a.m. message we’ll 100% regret the next day.
But reality is different from fiction: JARVIS knows everything about Tony Stark because, well, it’s a movie.
Movies never confront the privacy nightmare of an AI having complete access to every corner of someone’s life.
What would happen in the real world? It’s a trillion-dollar challenge waiting to be solved.
Right now, AI agents are still in the early stages of development—posting on Twitter, creating anime avatars, cracking a few jokes. But that’s changing quickly. We’re on the brink of something much bigger.
To really help us, these AI agents need access to our most sensitive information.
Think about what JARVIS actually knows about Tony:
Complete financial picture—every account, every investment, every secret project.
Relationships—from conversations with his wife, Pepper Potts, to communications with the Avengers and enemies.
Health data—full biometrics, medical history, shrapnel near the heart.
Career secrets—not just the Iron Man suit, but all of Stark Industries’ intellectual property.
Now imagine giving that level of access to today’s AI agents. Would you feel comfortable? This isn’t a hypothetical wish list—this is the type of data AI will need to truly become our digital representation.
An AI financial advisor that doesn’t know your complete financial picture is just a glorified calculator.
An AI health assistant that doesn’t have your complete medical history? Just WebMD with a better UI.
In order for AI to go from a novelty to a necessity, we must solve the privacy dilemma.

Today's AI infrastructure often forces us into a dilemma:
Give up privacy for practicality
Give all your data to centralized AI companies;
Trust that they will keep your data secure (pray);
Accept that your data may be used to train models.
2) Keep privacy but sacrifice practicality
Stick to local AI models with limited functionality;
Miss advanced features;
Accept mediocre performance.
Take the example of an AI health assistant for cancer patients.
To provide meaningful support, it needs access to your full medical history, genetic test results, current treatment options, medication schedules, side effect reports, and even your private conversations about how you really feel.
Without strong privacy protections, you are essentially broadcasting your most private health struggles to unknown servers and employees.
Imagine your most vulnerable moments—your fears, your pain, your treatment decisions—being processed in plain text on a company’s infrastructure.
The real problem lies in how AI systems handle data.
When you use tools like ChatGPT or Claude, here’s what happens: Your data is sent to their servers → processed in plaintext → and potentially stored for future model training.
Yes, they have privacy policies and security measures. But at the end of the day, you’re still relying on trust.
When AI was just writing emails or generating cute cat pictures, this might have been acceptable. But as AI becomes more personalized and powerful, this privacy crisis becomes existential.
The solution is not just better encryption or a stricter privacy policy. It’s like installing locks on a house without walls.
We need to fundamentally reimagine how AI systems handle sensitive data. We need infrastructure that can:
Compute on encrypted data without exposing it
Provide cryptographic privacy
Decentralize trust so that no single entity holds all the power
The next wave of AI won’t just be about smarter models or faster performance. It will be about trust.
Can we build systems that are robust enough to handle our most sensitive data, and trustworthy enough for us to share it?
Can we create the privacy infrastructure that makes real-life JARVIS possible?
These questions will define the next chapter in AI.
Nillion's story begins here.

Nillion is creating a whole new paradigm called "blind computing".
Through it, you can have all the capabilities of advanced AI systems without exposing your sensitive data. It’s not just encrypted storage, but actual computation is done on encrypted data, so that data remains private from beginning to end—even to the infrastructure that processes it.
But to understand why this is revolutionary, we need to understand where current privacy solutions fall short.
(1) Beyond Traditional Privacy
Many existing privacy solutions are like locking your data in a safe—it’s safe at rest, but when you want to use it, you have to take it out.
Every time you compute something, you expose your data. It’s like carrying sensitive files across a crowded street every time you need to process them.
This “decrypt-compute-encrypt” process creates windows of vulnerability that sophisticated attackers can exploit. Even with strong encryption, your data is exposed during computation, making it vulnerable to memory scraping, side-channel attacks, and other vulnerabilities.
Nillion’s blind computation enables computation on data in an encrypted state.
(2) The power of coordination
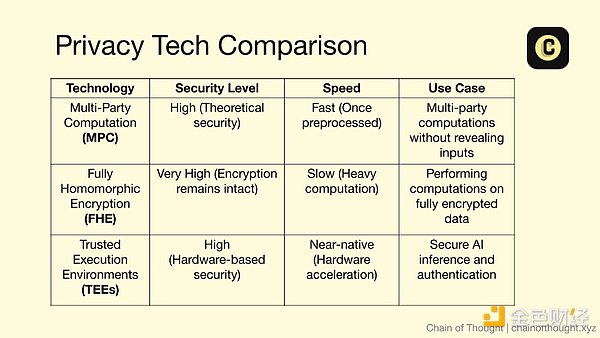
The current field of privacy protocols is fragmented and specialized. There is no shortage of solutions, but each has its limitations:
Multi-party computation (MPC) excels at secure distributed computing, but is difficult to scale.
Fully homomorphic encryption (FHE) supports computation on encrypted data, but is slow and costly.
Zero-knowledge proofs (ZKPs) provide strong verification without exposing data, but are limited by computing power and bandwidth.
Trusted Execution Environments (TEEs) provide practical security but require hardware trust assumptions.
Most projects choose an approach and optimize around its strengths while accepting its limitations. It's like choosing one instrument and trying to play an entire symphony.
Nillion isn't content to play solo. It's conducting the entire orchestra.

These privacy-enhancing technologies (PETs) work together to create a privacy solution that is greater than the sum of its parts.
Let’s dive into how Nillion achieves this technically.
The Nillion network architecture consists of two key components, each of which has a unique and important role:
Coordination Layer (nilChain)
Petnet (Privacy Enhanced Technology Network)
Together, they enable blind computation.
(1) Coordination Layer
The coordination layer built on the Cosmos SDK, called nilChain, acts as the control center of the network. It does not process private data or run computations. Instead, it ensures that the network runs efficiently and securely, like a high-performance operating system that manages processes and resource allocation.
Why Cosmos SDK?
The Cosmos SDK was chosen for its modular architecture, high scalability, and interoperability. Cosmos is designed for sovereignty, allowing nilChain to operate independently while benefiting from cross-chain compatibility through Inter-Chain Communication (IBC).
In practice, this means that Nillion can interact with other blockchain ecosystems securely and efficiently without relying on traditional bridges, which are often security risks.
What nilChain does
Despite being built on Cosmos, nilChain is intentionally kept lightweight. It does not store or process any sensitive data. Instead, it focuses on:
Payment processing — every time someone uses Nillion’s computing services, nilChain handles the economic logic — like a decentralized billing system.
Rewards and staking — node operators stake tokens to participate; in return, they receive fees for their honest work. Malicious nodes can lose their stake.
Network security — nilChain also maintains a global ledger of node stakes, reputations, and tasks.
Coordination — nilChain coordinates which node clusters handle specific computations, ensuring load balancing and assigning tasks to nodes with appropriate capabilities (e.g., clusters specialized in handling large-scale MPC).
This minimalist approach is crucial because it enables the coordination layer to focus entirely on coordination, leaving complex privacy-preserving computations to the Petnet.
As of now, nilChain is running in a testnet environment, and the mainnet is expected to go live this month.
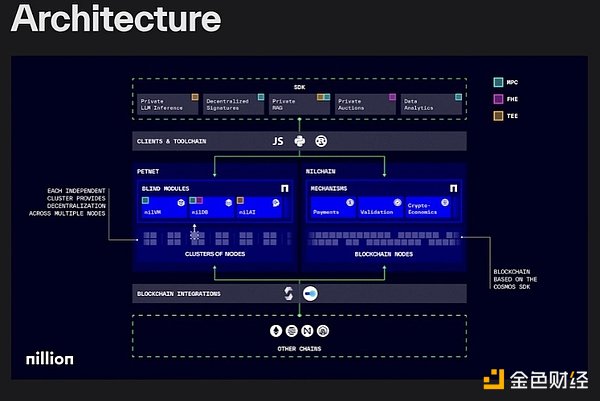
(2) Petnet
While the coordination layer manages the operations of the network, the Petnet (Privacy Enhanced Technology Network) is the real magic of Nillion.
It’s a network of specialized privacy processors, each contributing to a larger system that can perform computations on encrypted data without ever seeing the actual information.
Petnet combines different privacy technologies through a system of specialized clusters. Rather than forcing every node to handle every type of computation, nodes are grouped into clusters that specialize in specific tasks.
This cluster approach addresses a fundamental challenge in privacy-preserving computing: balancing security and performance.
Some computations require maximum security and can tolerate slower speeds, while others require lightning-fast processing for real-time applications. By letting clusters be specialized, Nillion achieves the best of both worlds.
Think of these clusters like specialized departments in a company. Just like you wouldn’t let your accounting team handle product design, you don’t want every node trying to handle every type of computation. Some clusters might focus on:
Maximum security for highly sensitive data
Real-time processing for time-critical applications
Best performance for specific types of computation
Petnet combines three cutting-edge privacy-enhancing technologies (PETs) to provide higher levels of security and efficiency.
(1) Multi-party computation (MPC)
MPC allows multiple parties to jointly compute a function while keeping their respective inputs private. Nillion’s custom MPC protocol is designed to eliminate the communication overhead of traditional MPC, which makes typical MPC slow.
How it works – Instead of one entity processing sensitive data, multiple nodes hold fragments (called “particles”) of encrypted information. Each node processes only its shares of data, ensuring that no single entity can reconstruct the original input.
Secret Sharing and Blinding – Private input data is split into multiple encrypted shares (shares) using Shamir’s secret sharing and one-time masks, preventing unauthorized access.
Local Computation without Interaction – Nodes compute independently without communicating with each other, preventing data leakage in the process.
Reconstruction and Verification - After the computation is complete, nodes combine their result shares to reconstruct the final output, ensuring correctness without exposing sensitive inputs.
By removing communication from the computation process, Nillion’s MPC achieves speeds and scalability that were previously considered impractical.

(2) Fully Homomorphic Encryption (FHE)
Fully Homomorphic Encryption (FHE) allows computation on encrypted data without decryption. While FHE is computationally expensive, Nillion selectively integrates FHE to leverage it where it is most valuable.
Why FHE? —Unlike MPC, which splits data between nodes, FHE enables computation directly on encrypted data without secret sharing.
FHE as a complementary module —Nillion uses FHE in situations where secret sharing is not feasible, such as financial transaction computations that must remain encrypted end-to-end.
MPC + FHE —In some cases, FHE is used in conjunction with MPC, allowing the system to encrypt data before it is shared across nodes. This ensures that data remains encrypted at every stage of processing.
The network also integrates pre-processing techniques to reduce the complexity of homomorphic operations, making FHE feasible in practical deployments.
(3) Trusted Execution Environments (TEEs)
TEEs provide hardware-based isolation for secure execution of sensitive computations within the processor. Nillion selectively leverages TEEs through its nilTEE framework.
How TEEs work—TEEs are secure areas within the processor that isolate running code and prevent sensitive data from being exposed to the wider system.
AI Model Execution—TEEs support secure AI model inference without exposing model weights or input data.
Threshold Signatures and Authentication - For secure cryptographic signatures and authentication.
Short-term secure computation - Nillion uses TEEs only for performance-critical tasks, ensuring long-term data protection remains decentralized.
By integrating TEEs with MPC and FHE, Nillion strikes a balance between performance, security, and decentralization, ensuring computations remain private while delivering high-speed results.
All this sophisticated privacy technology will be useless if developers can’t use it easily.
That’s why Nillion created a set of development tools that abstract away the complexity of privacy-preserving computation.
The current toolkit includes the following components:
(1) nilVM:
A privacy-first virtual machine that changes the way developers write secure applications.
Using a Python-based language called Nada, developers can write code that feels like regular programming—but behind the scenes, it compiles to privacy-preserving operations. Think of it as a universal translator that converts regular instructions into secure multi-party computations without the developer having to worry about cryptography.
The VM supports basic operations and more complex tasks like threshold signing of messages, making it particularly suitable for financial applications that need to handle sensitive data while maintaining privacy.
This module can be accessed through the SecretSigning SDK, which leverages the cryptographic capabilities of nilVM for threshold signing and authentication workflows.
(2) nilDB:
nilDB makes working with encrypted data as simple as using a regular database. Unlike traditional systems, where data must be decrypted before it can be queried or analyzed, nilDB keeps all information encrypted while still allowing complex operations.
It uses a combination of secret sharing and MPC to split data across multiple nodes, ensuring that no single node sees the complete information.
Developers can write familiar SQL-like queries, and nilDB automatically handles all privacy-preserving operations.
This makes it ideal for healthcare systems that need to analyze patient data while maintaining strict privacy compliance, or financial services that need to detect fraudulent patterns without exposing individual transaction details.
The system even supports secure multi-party analysis, allowing organizations to gain insights from combined data sets without revealing their underlying data to each other. It can be accessed through the following SDKs:
SecretVault: A vault-like service for securely uploading and managing encrypted data.
SecretDataAnalytics: Allows authorized query or analysis of encrypted data sets without exposing the underlying information.
(3) nilAI:
A set of privacy technologies focused on AI that makes private machine learning practical. It contains three key components:
AIVM (AI Virtual Machine): Based on Nillion's MPC technology and integrated with Meta's CrypTen framework, it enables AI models to process data while keeping the model and data private.
nada-AI: Provides a PyTorch-like interface that enables developers to easily work with privacy-preserving AI models. You can train neural networks, run inferences, and handle machine learning tasks using familiar patterns.
nilTEE: Secure AI processing using a trusted execution environment, especially suitable for running large language models privately.
The system accelerates encrypted AI operations using techniques such as discrete wavelet transforms (researched in conjunction with Meta's AI research team). This enables practical performance for running complex AI workloads - from personalized AI assistants that keep user data private to enterprise AI systems that need to maintain data confidentiality while providing real-time results.
From Request to Result: End-to-End Flow
Now that we understand how nilChain, Petnet, and blind modules work together, let’s look at a typical user interaction — from storing data to running an AI model.
Here’s the high-level flow:
1) User InitiationA user or application interacts with Nillion’s SecretSDK or API (e.g., “securely store this file” or “run this function on my data”).
2) Client PreparesThe SDK encrypts or secretly shares the data so that no single party can see it in its entirety. This may involve MPC shares or encapsulating the data for TEE processing.
3) Coordinated by nilChainRequests are sent to nilChain, which records the request, processes the $NIL payment, and assigns the task to specialized clusters in the Petnet. Different clusters may specialize in storage (nilDB), computation (nilVM), or AI reasoning (nilAI).
4) Blind Execution in Petnet
nilDB (Storage): Data shares are distributed among the nodes of the cluster.
nilVM (Compute): Nodes run the MPC protocol on their data shares - no single node sees the full input.
nilAI (AI Reasoning): TEEs or hybrid FHE/MPC approaches ensure that even node operators cannot see the raw data or model weights. During this phase, each cluster node processes only encrypted or masked data.
5) Results and Settlement
The cluster completes the results (e.g., storing shares, returning computational results, or sending encrypted AI responses).
nilChain confirms completion, releases payments to participating nodes, and handles penalties for any malicious behavior. Users ultimately decrypt the results locally (if necessary).
This workflow provides end-to-end privacy and verifiability, with nilChain coordinating tasks and Petnet executing securely behind the scenes.
Nillion technology is already processing a large number of workloads and has gained widespread attention from developers. Fortunately, this is not just theory.
Developer adoption is growing rapidly, and the Nillion SDK has been downloaded 961 times externally in just two months - an early signal of the platform's emerging developer ecosystem.
By providing a foundation for privacy-preserving computation and storage, Nillion is unlocking entirely new categories of products and services across multiple sectors.
Here are some examples:
(1) Private AI Agents
As mentioned earlier, the next wave of AI agents will need to process increasingly sensitive data to be truly useful. Nillion’s blind computation infrastructure enables AI agents to process private information without exposing it:
· Skillful AI has implemented private retrieval-augmented generation (RAG) using nilVM, allowing users to leverage sensitive documents during inference while minimizing data exposure.
· Rainfall has built its own AI platform focused on collective social intelligence while protecting user privacy through secure weight aggregation.
·Verida is developing a personalized AI chatbot trained on sensitive user messages, using nilDB for secure storage.
This shift from entertainment-oriented AI agents to utility-oriented AI agents often requires bullet-proof privacy guarantees that only blind computing can provide. As AI agents evolve to handle investments, governance, and negotiations, Nillion’s infrastructure becomes critical.
(2) Medical Applications
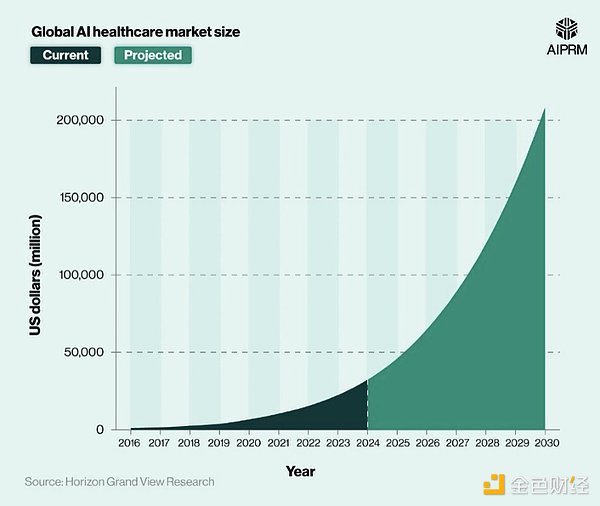
Medical is another huge opportunity for blind computing, and the AI medical data market is expected to grow from $32.3 billion in 2024 to $208.2 billion in 2030, a 524% increase.
· Secure research collaboration:Healthcare institutions can analyze patient data across regions without exposing sensitive information. · Privacy-preserving diagnostics:AI-based diagnostic tools can process patient data while maintaining complete confidentiality. · Compliant data sharing:Enable collaboration while meeting strict medical privacy regulations.
HealthBlocks demonstrates this potential by allowing users to collect data from different sources while maintaining ownership and control, and then use Nillion to generate insights for third parties without revealing specific details.
(3)DeFi and Sensitive DataCurrently, DeFi’s transparency exposes traders to the risk of MEV attacks, front-running, and market manipulation. Kayra, a decentralized dark pool DEX, addresses this issue by using Nillion’s blind computation to enable private, institutional-grade trading. · Secret order book: Orders are encrypted and processed privately, preventing market influence. · Blind computation matching (nilVM): Orders are submitted in encrypted form and processed using Nillion’s MPC nodes. Each node computes on a fragment of data without seeing the full order, ensuring confidentiality. When a match is found, only the final transaction details are decrypted for settlement, preventing leakage at every stage. · MEV and front-running protection: Orders remain private until execution, ensuring fair pricing.
By using Nillion, Kayra provides trustless privacy, making DeFi viable for institutions and large traders. If successful, it could revolutionize on-chain private transactions.
Other DeFi applications using Nillion include: · ChooseK is developing an order book platform to support private DeFi products. · Kagami created a trading strategy engine in nilVM for crypto financial strategies.
With the World Economic Forum estimating that $867 trillion could flow into DeFi, privacy-preserving infrastructure becomes critical for institutional adoption.
(4)Blockchain IntegrationNillion has also established strategic partnerships with major blockchain platforms to make blind computation accessible on these chains:· Arbitrum:Privacy tools to enhance Ethereum scaling· NEAR Protocol:Privacy-preserving application development· Aptos:Privacy-focused application infrastructure· Sei:Native integration for secure computation
These integrations allow smart contracts and users to leverage blind computation directly from their favorite chain, using native gas tokens - no new wallets required.
(5)Key Partnerships to Drive AdoptionTechnology is meaningless if no one uses it. Strategic partnerships are accelerating Nillion’s adoption across multiple sectors, with major collaborations showcasing the diversity and potential of the platform. The collaboration with Meta’s AI research team has achieved breakthroughs in privacy-preserving AI computing, while the AI agent co-ownership collaboration with Virtuals Protocol and the decentralized AI reasoning collaboration with Ritual demonstrate Nillion’s ability to push boundaries in emerging fields.
Combined with its strong technical foundation and growing ecosystem adoption, these strategic alliances enable Nillion to capture significant value as privacy-preserving computing becomes necessary infrastructure.
The NIL token is the core of the Nillion blind computing network, serving as both the utility token of the network and the governance mechanism. With a total supply of 1 billion, NIL aims to align the incentives of all network participants while achieving sustainable growth of the ecosystem.
Note: The NIL token is not yet live at the time of writing.
(1) Supply Side: Allocation and Unlocking
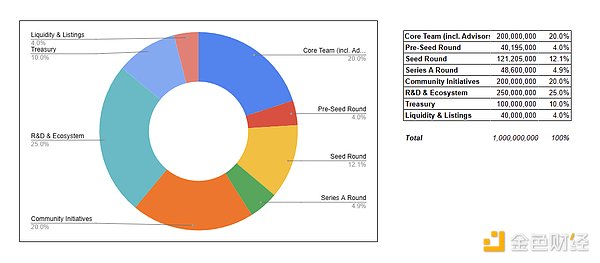
Token AllocationThe majority of the token supply (45%) will be used for community and R&D to continuously improve the technology, demonstrating a focus on sustainable growth rather than short-term gains. The protocol also reserves 7.5% of the total supply (75 million NIL) for the Genesis Airdrop to early supporters and builders, targeting those who have made meaningful contributions to the development of the network.
Unlock Schedule
Token release will follow a planned unlock schedule:
Initial circulating supply is approximately 13.9% (139.6 million tokens)
Major unlock event begins 6 months after genesis, reaching ~30% of supply
Gradually increasing to ~48% by 12 months after TGE
Long-term linear vesting of team and ecosystem allocations
(2) Demand Side: Utility and Governance
NIL plays a core role in securing the network and providing access to its services:
Network Access
Computation and Storage Operations: In the initial phase, users burn NIL tokens based on a USD-denominated credit system. Payments for all Petnet operations are currently 100% burned.
Module-specific pricing: nilVM: fixed rate burn for compute/storage operations, with the option to pre-burn tokens on specific clusters for credits to reduce latency; nilDB and nilAI: subscription-based model, requiring monthly burn of NIL to access the API.
Predictable costs: operations are priced in USD-denominated non-transferable credits, ensuring cost stability for the enterprise.
Node Staking
Validators and Petnet Clusters: Node operators stake NIL to protect their roles and may face slashing for malicious behavior. As the value of NIL grows, the network theoretically becomes more secure through higher economic penalties.
Governance and Resource Allocation
Proposals and Voting: NIL holders influence protocol upgrades, fee structures, and ecosystem funding.
Resource Deployment: Governance sets parameters for community resource allocation.
In the early stages, 100% of all Petnet operating fees were destroyed, creating a significant token destruction pool as network usage grew. Operating fees are set through governance decisions, with plans to transition to a permissionless, cluster-based pricing model in the future.
This combination of predictable, USD-denominated costs and full token burn creates a clear and strong connection between network adoption and token value. This is exactly what we like to see in token design.
Nillion’s token economics are built for the long game. Designed to thrive as network adoption expands, the system relies on three key drivers of sustainability:
Use → Value: As network activity grows, more tokens are burned, driving NIL price higher.
Staking → Security: Rising token value incentivizes node operators to stake more tokens, increasing the security and resiliency of the network.
Governance → Alignment: Token holders play a direct role in setting network policy, ensuring that those with a vested interest guide its development and long-term success.
If the network captures a small portion of the $270 billion cloud computing and storage market, token burns generated by network usage could quickly exceed the most aggressive unlocking schedule - powering the long-term value creation of the NIL token.
Nillion has assembled a truly world-class team that combines deep expertise in cryptography, distributed systems, and product development.
The leadership team brings together veterans from Web2 and Web3:
Alex Page (CEO) comes from a traditional finance background, having served as a general partner at Hedera SPV and as a banker at Goldman Sachs.
Andrew Masanto (CSO) is a serial entrepreneur with multiple exits and brings valuable ecosystem building experience as a co-founder of Hedera and founding CMO of Reserve.
The technical foundation is laid by several key leaders:
Dr. Miguel de Vega serves as Chief Scientist, bringing deep expertise in data-optimized cryptography with 30 patents. His research background is crucial to Nillion's innovative approach to privacy-enhancing technologies.
Conrad Whelan is the founding CTO, leveraging his experience as a founding engineer at Uber to build scalable distributed systems. His experience building services that serve millions of users is particularly valuable as Nillion aims to become core infrastructure.
We can at least tell that the team is very strong and has been building together for many years. All signs point to a bright future.
In terms of financing, Nillion has received a lot of financial support to realize its vision.

They have raised $50 million from well-known crypto investors including Hack VC, Hashkey Capital, Distributed Global, and Maelstrom. With an experienced team and significant financial support, Nillion is ready to take on the complex (and ambitious) challenge of building a privacy-preserving computing infrastructure.
(1) Orchestration is the Real Moat
Nillion’s approach is to focus on orchestrating multiple privacy-enhancing technologies (PETs) rather than betting everything on a single approach. This strategy is smart for two key reasons:
First, it creates selectivity. Different use cases have different privacy needs and trade-offs. Some prioritize speed over maximum security, while others require regulatory compliance or specific encryption standards. By orchestrating multiple PETs, Nillion can provide the right tool for each job rather than forcing everything through a one-size-fits-all solution. Second, it future-proofs the platform. As new privacy technologies emerge (and they will), Nillion can integrate them into its orchestration layer without disrupting existing applications. This adaptability will be critical as advances in quantum computing advance today’s privacy technologies.
Of course, building an effective orchestration layer is not easy. The challenge is making it seamless for developers. If the experience is too complex or clunky, Nillion’s powerful solution may be impressive in theory but unusable in practice.
(2) Privacy as infrastructure, not feature
The conclusion after reading this article should be that Nillion is positioning privacy as the infrastructure for the next generation of computing. Think about how SSL/TLS became the default for network communications. We no longer talk about “encrypted websites” because encryption is how the web works. Nillion’s bet is that blind computing will follow the same trajectory. As AI agents become more integrated into our lives and take on increasingly sensitive tasks, privacy will no longer be optional—it will be a prerequisite. Just as no serious business today would launch a website without HTTPS, future applications will not be able to function without built-in privacy guarantees.
Timing will be key. Enter too early, and the market may not feel the urgency yet. Enter too late, and centralized solutions may become entrenched. Nillion's success will depend on entering the market at the right time - when privacy issues have become so acute that developers and businesses begin to actively seek solutions. If they can catch this wave, Nillion has a real chance to make privacy-preserving computing the default standard for the next generation of applications.
Nillion is tackling the biggest obstacle to AI: trust.
By seamlessly integrating cutting-edge privacy technology with AI, Nillion has the potential to become the foundation of AI, just like SSL is to the web. If Nillion can make it both powerful and easy to use, it will drive the next wave of AI adoption. High risk, but huge opportunity. The privacy revolution has just begun. Let's wait and see!
The company is only the fourth entity that has been approved to offer crypto services to UK customers.
 Clement
ClementAs convicted traffickers deliberated over the optimal offshore haven for their crypto wealth, US authorities listened in and pounced on the proceeds accrued through illicit darknet drug sales.
 Catherine
CatherineProShares CEO Michael Sapir stated that the new ETF was created specifically to help people short ETH.
 Clement
ClementSingapore's cryptocurrency industry, once booming, faced a significant setback in 2022 due to a $2 trillion market crash and regulatory actions. However, the city-state remains focused on balancing innovation and investor protection in its evolving crypto landscape.
 Joy
JoyThe jury took less than five hours to reach their guilty verdicts.
 Clement
ClementInstead of requiring users to write complex queries with programming skills, individuals can now ask questions in plain language using Dune's natural language engine.
 Davin
DavinThe security of Tellor's X account was compromised by a sophisticated phishing scam that enticed users with fraudulent airdrop offers.
 Kikyo
KikyoBRICS nations unveils plans for their collective currency, shaping the future of global finance.
 Hui Xin
Hui XinThis collaboration has a clear objective: an Ethereum-based marketplace that stands as a testament to its dedication to preserving the rightful royalties of NFT creators upon each sale.
 Catherine
CatherineBitfinex encountered a minor phishing attack, reassuring users of their security measures while resolving the issue and collaborating with law enforcement for a comprehensive investigation.
 Hui Xin
Hui Xin