Author: Onkar Singh, CoinTelegraph; Compiler: Wuzhu, Golden Finance
1. What is a multi-signature cold wallet?
Multi-signature (multisig) cold wallets are generally considered one of the safest ways to store digital assets, providing additional protection against theft. However, even these advanced security measures are not foolproof, as demonstrated by the Bybit hack in February 2025.
Before we delve into their security, let's analyze what a multi-signature cold wallet is.
Cold Wallet Explanation
A cold wallet is a cryptocurrency storage method that is kept offline and disconnected from the internet. This setup makes it more difficult for hackers to access funds remotely. Examples include:
Hardware wallets (e.g. Ledger, Trezor)
Paper wallets
Isolated computers (devices that are never connected to the internet).
Cold wallets reduce the risk of cyberattacks such as phishing or malware by keeping private keys offline. But what is multisig?
Let’s take a look.
Multisig explained
Multisig technology requires multiple private keys to approve transactions, while single-signature wallets only require one key. Think of it as a joint bank account, where any withdrawal requires two or more signers to approve.
Common multisig setups include:
2-of-3 multisig: Any 2 of 3 keys must approve the transaction.
3-of-5 multisig: Any 3 of 5 keys are required.
5-of-7 multisig: Any 5 of 7 keys must sign.
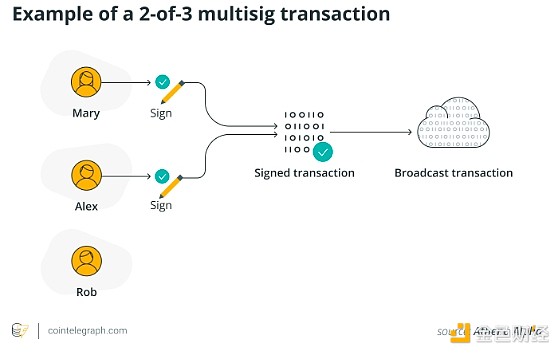
This extra layer of security means that even if one key is compromised, an attacker cannot unilaterally move funds.
Who uses multi-signature cold wallets?
Cryptocurrency exchanges: prevent internal fraud and unauthorized withdrawals.
Institutional investors: hedge funds and family offices that protect large amounts of cryptocurrency.
Decentralized Autonomous Organizations (DAOs): groups that manage shared funds through multi-signature governance.
How do multi-signature cold wallets work?
Multi-signature cold wallets require multiple private keys from trusted parties to approve and authorize transactions, enhancing security by preventing single points of failure.
To understand how a multi-signature cold wallet works, imagine a safe deposit box at a bank that requires two or more keys to open. No one person can access the contents alone - multiple trusted parties must be present.
Multi-signature cold wallets apply this concept to digital assets, adding additional security by requiring multiple private keys to authorize transactions.
Here is how it works in the crypto world:
Key Distribution: The wallet owner generates multiple private keys and distributes them to trusted parties or devices. For example, in a 3-of-5 multi-signature cold wallet setup, keys can be distributed to different roles to enhance security and accountability. For example, Key 1 may be assigned to the CEO as the primary decision-maker, while Key 2 is assigned to the Chief Financial Officer for financial oversight. The Chief Legal Officer holds Key 3 to ensure regulatory compliance, while Key 4 is stored in a secure, isolated location as an offline backup. Finally, Key 5 may be assigned to the Chief Security Officer, responsible for cybersecurity protocols.
Transaction Request:When someone wants to withdraw funds from a wallet, they must first create a transaction proposal—much like writing a check that requires multiple signatures to be processed.
Approval Process:The proposal is then sent to authorized signatories. In a 3-of-5 setup, at least three of the five key holders must approve the request, just like three different bank staff members needing to work together to unlock a safe. This process prevents any individual from making unauthorized transfers, even if one key holder is compromised or acts maliciously.
Broadcasting the Transaction:Once the required number of signatures have been collected, the transaction is broadcast to the blockchain network. Only then is the payment finalized and recorded on the public ledger. If the minimum number of approvals is not met, the transaction remains incomplete - just like a bank refuses to process a check without the required signatures.
3. How Multi-Signature Cold Wallets Suffer from Hacking
Despite the security advantages of multi-signature wallets, it is not immune to attacks. Hackers often exploit weaknesses in implementation, human behavior, or third-party services.
Let's understand further through some examples:
1. Supply Chain Attack (Bybit Hack, 2025)
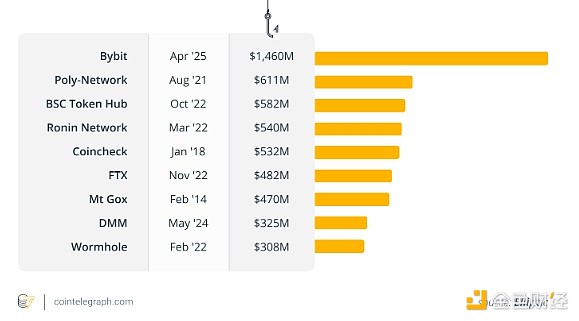
In February 2025, hackers hacked into the multi-signature process, causing the Bybit exchange to lose $1.5 billion worth of Ethereum.
The attack process is as follows:
Bybit uses a 3-of-5 multi-signature cold wallet, which means that any three authorized signatures are required to transfer funds.
The attackers compromised the infrastructure of a third-party wallet provider (SafeWallet).
They hacked into SafeWallet’s developer devices, injected malicious code, and altered the multi-signature process.
Bybit’s security team approved transactions that appeared legitimate, but in reality, funds were redirected to addresses controlled by the hackers.
This attack highlights the risks of relying on third-party providers for wallet security. Even if your private keys are safe, a compromised service can still put your funds at risk.
2. Social Engineering Attacks
Multi-signature wallets require human approval, and hackers can manipulate people.
For example, in 2022, hackers targeted senior employees of a crypto fund using phishing emails. Once the attackers gained access to their work devices, they used malware to record private key inputs. Since multi-signature only requires 2-of-3 approvals, the attackers bypassed security.
3. Rogue Insiders and Collusion
A multi-signature system is only as good as its participants. If the malicious employee is part of a 2-of-3 or 3-of-5 setup, they could collude with the hacker to sign fraudulent transactions.
For example, in 2019, an exchange executive conspired with an attacker to approve $200 million in unauthorized withdrawals. This incident led to a shift toward more decentralized signing methods.
4. Smart Contract Vulnerabilities
Some multi-signature wallets integrate smart contracts to automate transactions; however, if the smart contract contains a coding error, an attacker can exploit it.
For example, in 2017, a bug in the Parity Multisig Wallet caused hackers to freeze more than $150 million worth of ETH, rendering the funds unavailable.
4. How to Make Multi-Signature Cold Wallets Safer
To make multi-signature cold wallets safer, use a higher signing threshold, implement multiple layers of authentication, and store keys in secure, geographically dispersed locations.
As mentioned above, multi-signature cold wallets are still one of the best security solutions, but you must take extra precautions to minimize risk, including:
Use higher thresholds (e.g., 4-of-7 instead of 2-of-3): More signatures required = harder for an attacker to crack enough keys.
Implement multiple layers of authentication: Combine passwords, biometrics, and hardware security modules (HSMs) to access keys.
Shamir’s Secret Sharing: Split private keys into multiple pieces that need to be reconstructed to use the original key.
Isolate signing devices: Use offline devices to sign transactions to prevent remote hacking.
Distribute keys geographically: Store keys in different locations or with separate custodians to avoid single points of failure.
Key rotation strategy: Regularly change key holders and regenerate keys to reduce the risk of access theft.
Regular security audits: Hire third-party experts to review your wallet settings and detect vulnerabilities.
Independent co-signers: Involve an external security company or a trusted third party as one of the signers to prevent internal collusion.
Access logs and alerts: Use a logging system to monitor key usage and receive alerts on suspicious activities.
Multi-party computation (MPC): Use cryptographic protocols where private keys are never fully assembled, adding an extra layer of security.
V. Are multi-signature cold wallets still worth it?
Multi-signature cold wallets are still one of the best options for those who want to protect their cryptocurrency assets from theft and fraud. However, their complexity and potential vulnerabilities should not be ignored, especially in the case of supply chain attacks.
Yes, multi-signature cold wallets are still one of the best and safest options for storing large amounts of cryptocurrency. However, they are not foolproof.
The February 2025 Bybit hack was a wake-up call: even sophisticated multi-signature cold wallets can be compromised through a supply chain attack, where attackers exploit vulnerabilities in the systems or hardware used to generate or store private keys.
The attack highlighted the importance of not only relying on the technical setup of a multi-signature wallet, but also considering the broader security ecosystem, including the physical security of the device and the integrity of the key management process.
So, while multi-signature cold wallets offer strong protection, they also come with their own set of challenges. The complexity of setting up and managing a multi-signature system, the risk of key loss, and potential vulnerabilities to physical threats can present difficulties, especially for inexperienced users. Additionally, a slower transaction approval process can be inconvenient when time is of the essence.
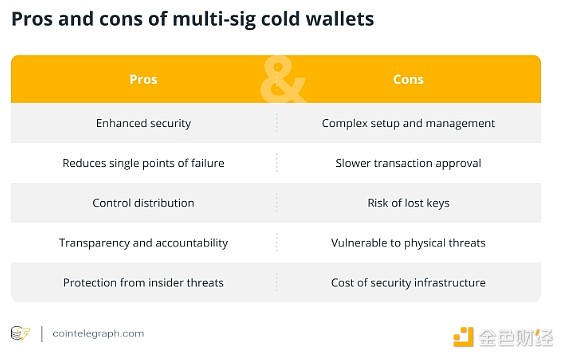
Ultimately, deciding whether a multi-signature cold wallet is the right choice for the security of your digital assets comes down to weighing its benefits against its limitations. If you manage a large amount of cryptocurrency assets and can handle the complexity, a multi-signature wallet can provide a high level of security that is difficult to match with traditional wallets. On the other hand, if you are not prepared to invest in the necessary infrastructure or cannot safely manage multiple keys, a simpler wallet solution may be more appropriate.
It is also important to remember that no security measure is completely risk-free. As seen with recent hacks, the broader security environment plays an important role in protecting your assets. In order for a multi-signature cold wallet to be truly effective, key holders must remain vigilant, maintain strong cybersecurity practices, and regularly assess potential risks.
 Aaron
Aaron
 Aaron
Aaron Aaron
Aaron Joy
Joy Catherine
Catherine Kikyo
Kikyo Joy
Joy Catherine
Catherine Aaron
Aaron Hui Xin
Hui Xin Alex
Alex