GMX suffered an attack.The attacker exploited a reentrancy vulnerability in the project contract and made a profit of approximately US$42 million. The Beosin security team conducted a vulnerability analysis and fund tracking for this attack, and shared the results as follows:
Detailed attack steps
The attacker first exploited the margin refund mechanism in the executeDecreaseOrder function in the OrderBook contract, and launched a reentrancy attack to bypass the Timelocklever switch of the contract:
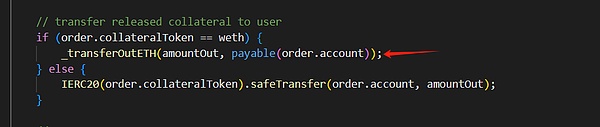
Then, the attacker borrowed USDC through flash loans to pledge and mint GLP, and at the same time increased BTC short positions with USDC as margin, causing the AUM value of the GLPmanager contract to be artificially high. The calculation of this value will affect the price of GLP.
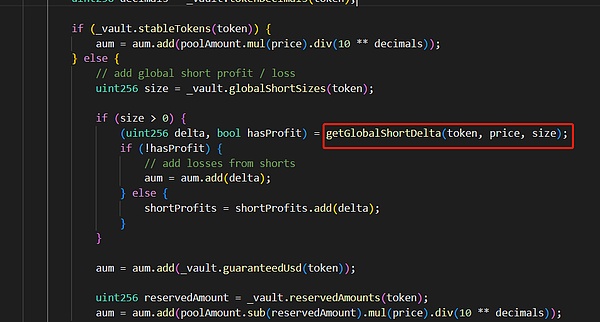
Finally, the attacker redeemed GLP at an abnormal price for profit and specified that it be exchanged for other tokens.
Vulnerability Analysis
Through the above attack process, we can see that the reasons for the vulnerability exploitation of the entire incident are as follows:
- Lack of reentrancy protection, resulting in reentry and modification of internal states during the redemption process.
- The redemption logic is relatively complex and lacks sufficient security checks.
Although GMX has undergone multiple security audits, this reentrancy vulnerability was still ignored. If the redemption logic is checked more strictly and possible reentrancy vulnerabilities are taken into account, such security incidents may be avoided. Stolen funds tracking Beosin Trace tracked the stolen funds and found that the attacker's address 0x7d3bd50336f64b7a473c51f54e7f0bd6771cc355 made a profit of about 42 million US dollars. The DeFi protocol then exchanged stablecoins and altcoins into ETH and USDC, and transferred the stolen assets to the Ethereum network through multiple cross-chain protocols. Currently, about 32 million ETH worth of the stolen assets are stored in the following four Ethereum network addresses:
- 0xe9ad5a0f2697a3cf75ffa7328bda93dbaef7f7e7
- 0x69c965e164fa60e37a851aa5cd82b13ae39c1d95
- 0xa33fcbe3b84fb8393690d1e994b6a6adc256d8a3
- 0x639cd2fc24ec06be64aaf94eb89392bea98a6605
Approximately $10 million in assets are deposited at the address of the Arbitrum network0xdf3340a436c27655ba62f8281565c9925c3a5221. Beosin Trace has added the hacker's related addresses to the black address database and will continue to track them in the future.
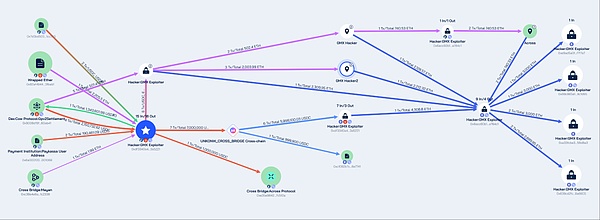
According to Beosin Trace analysis, all stolen funds are still stored in multiple addresses of the attacker
Summary
The core of this attack is that the GMX contract has a reentrancy vulnerability, which allows the attacker to redeem a large amount of assets for profit through the false increase in AUM value. Complex DeFi protocols like GMX require comprehensive and multi-level security audits to thoroughly test and review the contract code. Previously, the Beosin security team has completed security audits of multiple DeFi protocols (such as Surf Protocol, SyncSwap, LeverFi, and Owlto Finance), focusing on discovering contract logic defects and extreme situations that may be overlooked, ensuring that DeFi protocols are fully tested.
 JinseFinance
JinseFinance






