Author: Shew & Noah, DeepSafe Research
Since the birth of Bitcoin and Ethereum, the Crypto industry has been circulated with the saying of "Impossible Triangle". This well-known law predicts the conflict between trustlessness and high efficiency. Although there have been endless solutions such as payment channels, Rollups and modular blockchains, none of them can be completely universal. If we want to build use cases for specific scenarios, such as customized programmable signatures, we have to introduce other technical solutions.
Now, with the continuous development and maturity of the industry, TEE (Trusted Execution Environment) has gradually been integrated into the Web3 ecosystem. By providing data isolation and integrity at the hardware environment level, TEE not only ensures security, but also brings new possibilities for application scenarios in Crypto.
In this article,DeepSafe Research will explore the application of TEE in Web3 through several cases such as TEE-Boost, Rollup-Boost, CRVA,to reveal its huge potential and new scenarios that may appear in the future.

What is TEE?
What is TEE?
What is TEE?

What is TEE?
What is TEE?
In layman's terms, TEE is a secure areaisolatedinsideaprogram leaf="">is executed in the TEE, and this program will not be interfered with by other programs including the operating system.
Unlike security measures at the software level, TEE uses special hardware to ensure that external entities cannot observe or access data within the TEE. Neither the host operating system running the TEE nor the cloud service provider can see the sensitive data within the TEE. This is security, one of the two major features of TEE. It can build a barrier for sensitive computing and data.
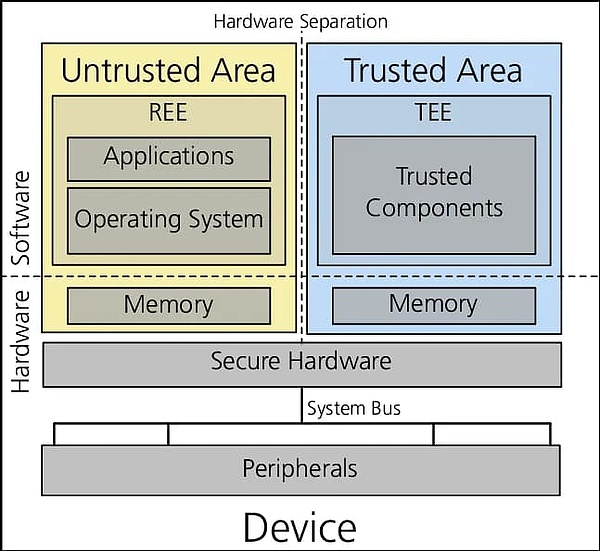
and the so-called integrity means that the code running in TEE is completely pre-compiled good logic . text="">Execution, there is no possibility of external manipulation. TEE hardware will provide the hash value of the code executed internally and the signature of the hash. Anyone who interacts with the TEE can check the hash value to determine whether the program running inside the TEE is incorrect.
For the signature mentioned above, there is a root key set by the hardware manufacturer in the TEE, which is specifically used to generate signatures. There are many ways to generate this key. One method is "key injection", in which the TEE chip manufacturer generates the key externally and then stores the key in the chip. The Intel SGX chip uses this method, so Intel, as a chip manufacturer, may know the content of the key.
Currently, a more novel method of generating TEE keys is to embed a random number module inside the TEE, and automatically read the random number and generate a key when the TEE is used for the first time. Since the current random number generator can generate true random numbers, even the chip manufacturer does not know the content of the key. In this way, no one, including the data center running the TEE server, can steal the key inside the TEE.
Most reference materials focus on the security of TEE, but less on integrity. In fact, integrity and its verification process are very important. We can verify the signature generated by the hash value of the TEE for the program. This process is generally called Remote Attestation. The figure below shows how users can ensure that the program executed in the TEE is consistent with the open source code on Github.
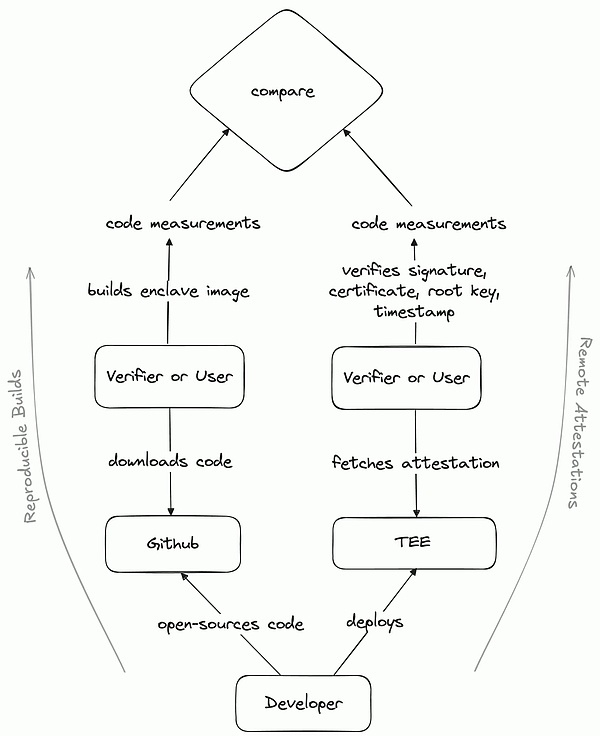
So for any TEE-related application, we can trust that the sensitive data in the application will not be stolen, and we can also verify that the application is executed according to its open source code. However, TEE is not completely trustless, and for programs using TEE, it is still necessary to trust the hardware vendor.
Since most TEE-enabled processors are produced by hardware manufacturers such as Intel, AMD, and ARM, users must trust that these vendors have implemented the complete process flow correctly and . There is no backdoor in the hardware. At the same time, users can perform the remote authentication described above to prevent the operator of the host where the TEE is located from placing the program in a non-TEE environment. Typical TEE application scenarios in Web3 TEE-Boost: Make the block building process more decentralized In the Ethereum ecosystem, TEE is used to solve the centralization problem of MEV. Most nodes in the Ethereum network are connected to a middleware called MEV-Boost, which is highly dependent on centralized Relay services. To better understand this, let us briefly introduce the workflow of MEV-Boost: 1. First, there are many Searchers in the Ethereum network, which read unchained transaction instructions from the public transaction pool to find MEV opportunities. Searcher will sort a batch of transactions into a list (inserting the transactions he initiated) and hand it over to Builder 2. Different Searchers need to bid, and Builder will select several non-conflicting transaction sequences and aggregate them into a block. The Builder will then declare how much tip will be paid to the block maker if the block is put on the chain
3. Relayacts as an intermediary and collects blocks submitted by multiple Builders. When Validator/Proposerproposes a block, it will request a block from Relay.Relay willselect the block with the most tips, andsendthe block headerto the Validator(Note that it is the block header, not the complete block. The block header only contains some summary information and the tip amount paid by the Builder)
4. Validator/Proposer signs the block header and broadcasts it to the network, expressing his approval of the block header submitted by Realy. After Relay confirms this, it will send the complete block to Proposer, who will assemble it and broadcast it for the second time to pass on the complete block.
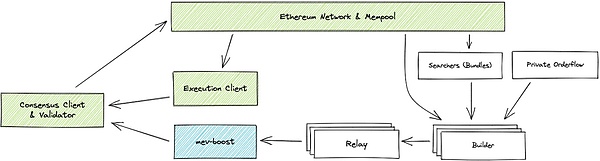
Observing the above process, it is not difficult to find that the role of the Relay service provider is very important. He must ensure the following points:
Privacy: Relay must ensure that the block producer does not see the data in the block in advance, otherwise the block producer can imitate the Searcher's transaction sorting method, construct a batch of MEV transactions by himself, and obtain all the benefits.
Block validity:Relay must ensure that the blocks submitted by the Builder are valid and do not contain garbage data.
Data availability:Relay must ensure that the complete content of the block is presented within a limited time, so that the Validator can successfully produce the block
Highest tip:Relay must ensure that the block it submits to the Validator is the one that allows the latter to receive the most tips
Although Realy is of great importance, MEV-Boost currently relies on highly centralized Relay service providers. As can be seen in the figure below, several major Relay service providers almost monopolize the entire MEV market. Ultra Sound alone accounts for almost 40% of the market share. The problem brought about by centralization is the potential for evil.
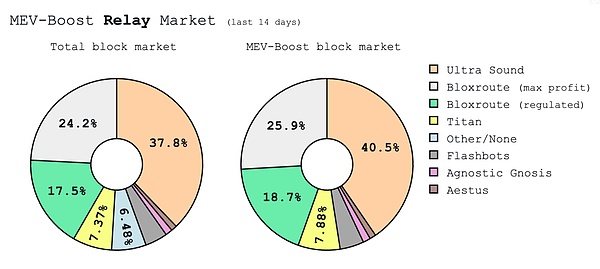
The simplest scenario is that the Relay service provider abandons the privacy protection principle and directly leaks the block content constructed by the Builder to the block producer in advance. At this time, the block producer can imitate the transaction sorting method of the Builder and Searcher and privately construct MEV transactions for his own profit. In addition, Relay's malicious scenarios also include submitting invalid blocks, withholding data, etc.
To solve the above problems, TEE-Boost proposes a revolutionary method that uses TEE to eliminate the trust assumption of Realy while retaining all security guarantees within the current MEV-Boost architecture. TEE-Boost abolishes the existence of the role of Relay, allows Builder to run code directly in TEE, through remote verification proven itself generated code Then the Proposer directly connects to multiple Builders, selects the block header with the highest tip and signs it, and then the Builder presents the complete block content. Since the Realy intermediary has been eliminated, the Builder does not have to worry about the early leakage of block content.
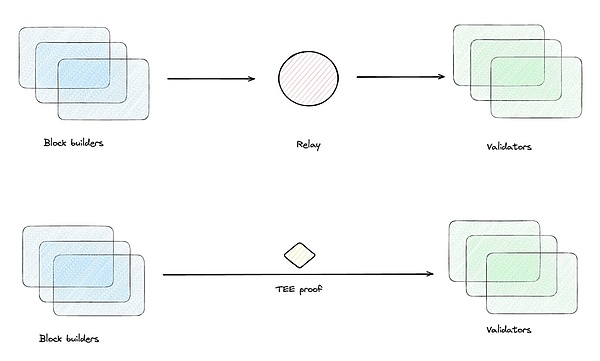
Rollup-Boost: Using TEE to extend Layer2
In addition to TEE-Boost, Rollup-Boost in the Ethereum ecosystem also uses TEE. Rollup-Boost is a Rollup construction solution jointly developed by Flashbot, Uniswap Labs and OP Labs. It is currently used in Unichain. It is a modular solution that implements two extension modules: 1. 250ms Confirmed “Flashblocks”: Provides an ultra-high transaction confirmation speed of 250 milliseconds.
2. Verifiable priority sorting: The transaction sequence is strictly sorted according to the priority fee paid for each transaction and will not be manipulated by the block constructor. In addition, smart contracts such as Defi are allowed to recover part of the MEV income
For Flashblocks, the core is to package the transaction in TEE and generate a block fragment to broadcast, while Unichain's validators will collect multiple fragments and package them into a complete block.
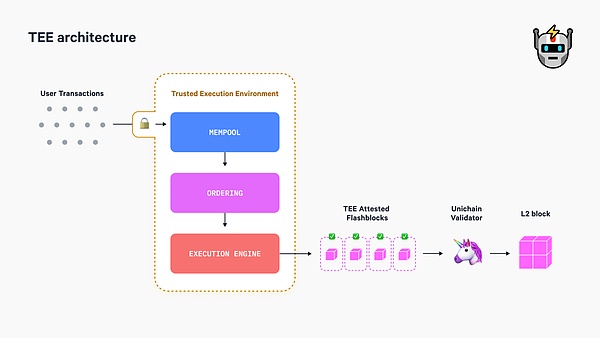
The benefits of this method are obvious. It allows the validator to receive part of the block data at all times, unlike in the past when it had to wait for the window period to receive the block. In this way, its bandwidth utilization will be significantly improved, which can increase TPS and speed up transaction confirmation.
In addition, Since the generation of block fragments is carried out within the TEE, as long as the program within the TEE does not contain errors, these block fragments will definitely be valid and will not contain junk data. In this way, Unichain's validators can also save the workload of verifying block data.
Verifiable priority sorting uses the characteristics of TEE to provide reliable transaction sorting results. Any third party can trust that the block-producing program running in TEE does not contain malicious logic. If the program is not executed in TEE, then the transaction sorting may not be completely carried out according to priority, and the block producer may manually adjust the transaction order for the sake of interest.
DeepSafe: A new generation of trustless threshold signature scheme
In order to achieve a more decentralized, trustless message verification + threshold signature scheme,DeepSafeintroduced TEE and ZK, and created an original full-process confidential lottery + signature scheme called CRVA (Crypted Random AI Verification Network).
In order to increase the speed of message verification and threshold signature, CRVA will randomly select nodes through a lottery algorithm, such as drawing 10 nodes as validators every half an hour to verify whether a message is valid (such as whether a cross-chain transaction is valid). After the target message is verified, the validators will generate a threshold signature and trigger subsequent operations.
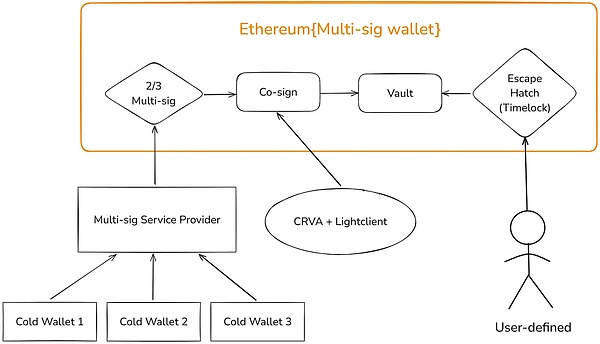
In CRVA, DeepSafe uses the privacy protection features of TEE and ZK to hide the identity of the validator and prevent internal collusion or hacker attacks. The specific workflow is simplified as follows: 1. The core module of each CRVA node runs in TEE, and a permanent public key is left on the DeepSafe official public chain to register the identity. 2. The node will generate a temporary public key in TEE and generate a ZK Proof to prove that the temporary public key is associated with a permanent public key on the chain, but it will not disclose which one it is (note that because of TEE, the node itself does not know the content of its temporary public key) 3. After that, the node encrypts the temporary public key in TEE, sends the ciphertext and ZKP to the outside world, and is received by Relayer. Relayer will decrypt the ciphertext in TEE and restore the temporary public key set (due to TEE, Relayer does not know which node submits the ciphertext corresponding to each temporary public key) 4. After decrypting the temporary public key set, the Relayer node will submit it to the chain and call the VRF function to randomly select several nodes as verifiers to form an anonymous committee 5. Assuming that there is a message (such as a cross-chain request) that needs to be verified, the CRVA network will broadcast the message to be verified. The node will first use the temporary public key in the TEE to verify whether it belongs to the committee, and then choose to participate in the signature style="text-align: left;">6. Currently, DeepSafe uses on-chain remote proof to ensure that the calculation process of the CRVA node is strictly carried out within the TEE. DeepSafe officially built a public chain specifically for receiving and verifying remote proofs generated by CRVA nodes. The core of this CRVA solution is that almost all important activities take place within TEE, and the outside world does not know what happened. leaf="">, they can only see a bunch of encrypted ciphertext outside TEE. No one, including the Relayer, knows which nodes are the validators, and even you don't know what your temporary public key is, which fundamentally prevents collusion and external attacks.
In theory, attacking DeepSafe's CRVA committee requires attacking hundreds of nodes in the entire CRVA network, which is very difficult. This trustless threshold signature scheme implemented by TEE and privacy computing can be applied to many scenarios such as multi-signature wallets, asset custody, cross-chain bridges, oracles, etc.
In previous articles, we mentioned that CRVA can construct a 2FA two-factor verification process on top of the verification process of conventional smart contract wallets to increase the security of user assets; in addition, most cross-chain bridges or asset management platforms adopt multi-signature/MPC custody methods, and CRVA is almost naturally suitable for such scenarios.
Bool Network, a well-known cross-chain bridge in the Bitcoin ecosystem, is built based on CRVA. The cross-chain bridge processed a total of more than US$350 million in cross-chain transactions in 2024, connecting to almost 80% of the Bitcoin Layer2 network, achieving good results.
Future applications of TEE
TEE coprocessor: connecting Web2 and Web3
TEE coprocessor is currently one of the most promising scenarios for TEE in the future. The so-called coprocessor refers to the use of provable off-chain computing to replace costly on-chain computing, similar to the idea of Rollup. We can execute complex calculations, data processing and algorithm operations in TEE and verify their results on the chain through cryptographic proofs.
This method can provide low-cost and private computing power for smart contracts in the EVM ecosystem. For example, the AMM contract has a complex algorithm that can calculate the best AMM parameters at present, but this algorithm consumes a lot of gas to execute on the chain. At this time, we can execute the algorithm in TEE, and when the AMM contract updates the parameters, it only needs to initiate a request to the program in TEE to receive the result directly.
In addition, we can also create new types of applications, such as Teleport, which uses TEE co-processing to allow smart contracts to control Twitter accounts. Users can authorize their Twitter to TEE for automatic operation. For example, we can trigger a transaction on the chain. When TEE monitors the transaction instruction, it will generate a tweet in TEE and then publish it to Twitter.
A more interesting method is to call the LLM API inside the TEE to implement complex conditional judgments. CurrentlyDeepSafeisexploringAI oracle based onTEE.The core part of the oracle is executed in TEE, which can call LLM to retrieve external data, output a conclusion about whether an event has occurred, and send the conclusion to the chain, so as to provide more accurate event results for the prediction market.
Encrypted memory pool and private transactions
Due to the confidentiality of TEE, we can build a completely private transaction processing workflow based on TEE. The traditional memory pool exposes the content of the transaction to everyone in the network, creating opportunities for various MEV attacks and damaging user interests. The developers of Rollup-Boost mentioned above are exploring this scenario.
TEE-based encrypted memory poolcan ensure that transactions are highly confidential throughout their life cycle, for example. Users directly submit encrypted transactions to the TEE-based sequencer, and the entire process of transaction decryption, sorting, and execution is carried out within the TEE and is not visible to the outside. Finally, we only publish the latest status changes after the transaction is executed to the blockchain.
TEE multi-prover system
In addition to the aforementioned scenarios, TEE can also act as a prover for Rollup as a technical supplement to ZK and OP. Well-known Rollup projects such as Scroll and Taiko have adopted TEE provers. This method is more efficient and faster than ZK and is also easy to iterate.
Conclusion
TEE represents one of the most important technological developments in the blockchain space, providing a practical path to resolving the long-standing tension between performance, privacy, and decentralization. By providing hardware-guaranteed isolation and integrity, TEEs are able to support new classes of applications while maintaining the trust-minimized properties that are unique to blockchain systems.
The applications explored in this article—from MEV-Boost’s decentralized block construction to Rollup-Boost’s performance improvements to DeepSafe’s advanced security mechanisms—demonstrate the transformative potential of TEE technology. These applications demonstrate that TEEs can deliver immediate, real-world benefits while laying the foundation for more ambitious applications in the future.
The future of blockchain infrastructure will likely not be limited to a single technology solution, but rather a complex combination of multiple technologies - each optimized for specific use cases and security requirements. TEEs will play a key role in this multifaceted ecosystem, providing the performance and functionality required to drive blockchain applications toward mainstream adoption while retaining their unique decentralized, trustless properties.
 Kikyo
Kikyo
 Kikyo
Kikyo Brian
Brian Brian
Brian Joy
Joy Brian
Brian Alex
Alex Alex
Alex Alex
Alex Kikyo
Kikyo Brian
Brian