Author: Liz & Reborn
Background
Yesterday, a user contacted the SlowMist security team and asked how to cancel the signature, and attached a screenshot showing that his wallet address hadrisk authorization.
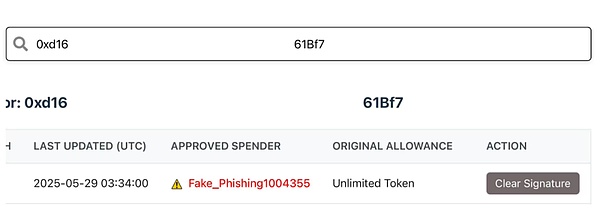
The user said that there was an authorization in his wallet that could not be revoked. There was no response after clicking it many times, and the wallet interface also displayed a risk warning. He also recalled that he had authorized a swap operation for a certain token many years ago, so he felt that this risk warning was not groundless.
A scam in the guise of security
The SlowMist security team used the block browser andRevoke to investigate, but did not find any risk authorization records for the addresses in the screenshots. Soon after, the user sent another screenshot showing the results of his query in a certain tool. Upon comparison, the addresses in the two screenshots were not consistent. We immediately suggested that the user provide the link to the tool together with the relevant addresses. At this point, the user also began to wonder: Could it be that both of his addresses have risk authorizations? We then analyzed the tool Signature Checker (http://signature[.]land) and found that it supports users to enter private keys for query. An address that was originally risk-free would also be risky if the private key was entered on this webpage.
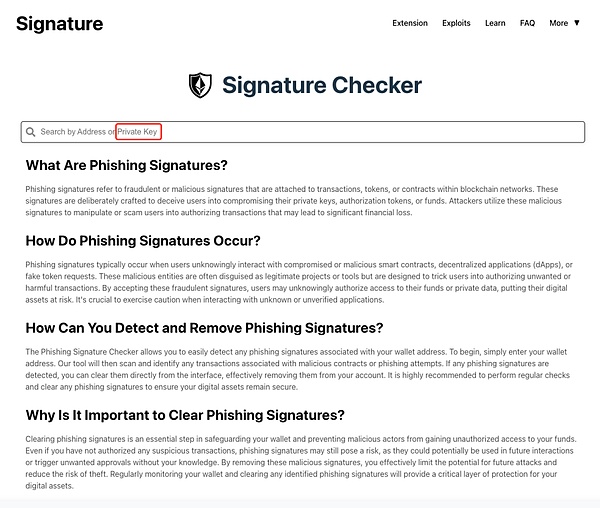
It is worth noting that the page design of this phishing website is very similar to the interface style and Logo of Revoke, which can easily lead users to mistakenly believe that it is a regular authorization revocation platform, thereby lowering their vigilance and increasing the risk of being deceived. The following is the official website interface of Revoke:
We used the tool provided by the scammer to query the user's two addresses and found that there was indeed a record of risky authorization. However, one of the rules in the dark forest is to remain skeptical and continue to verify. We continued to test and found that when we randomly pasted an address, the tool would show that the address had risky authorization, and the authorization time was very close to the query time. This design not only gave users hope, but also created a sense of urgency: it should be fine to cancel now.
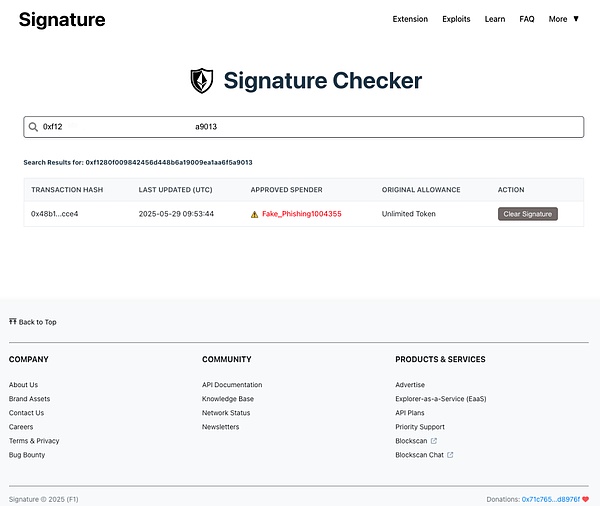
We then entered the private key for the test to query, and found that the page popped up a prompt of "wrong format", but the information we entered was still transmitted.
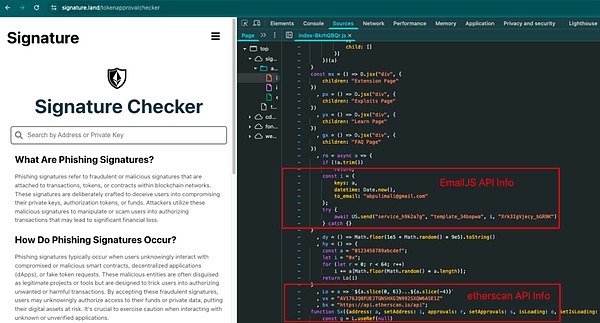
After analyzing the front-end code of the phishing website, we found that this phishing website used the EmailJS API to transmit information, and even used the Etherscan API to detect whether the address really exists.
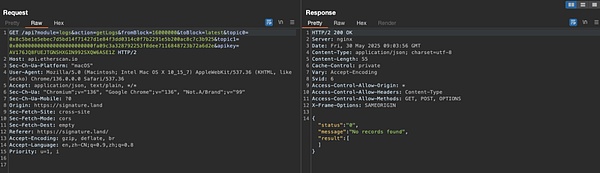
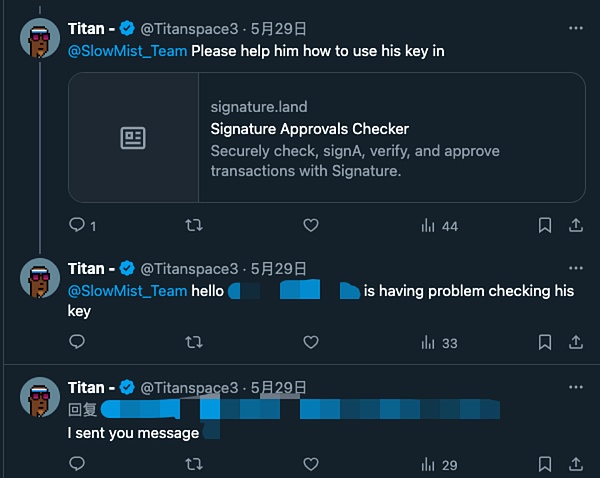
This is the request interface sent to EmailJS API. It can be found that the address or private key information entered by the user will be sent to the scammer's email address (abpulimali@gmail[.]com) through this interface. At this point, the scam is quite clear. According to user feedback, the scammer initially contacted him through the comment area and private messages of the X platform, and claimed in the conversation that "you signed a phishing signature", and then took the initiative to provide a link to the "revocation authorization tool".
From the chat records, the scammers are well versed in social engineering and deliberately put the unknown tool in front and the well-known Revoke in the back. People generally tend to click on the front link and find that the address is "risky". Even if they cross-verify with Revoke and find no abnormalities, they will suspect that Revoke has not identified it.
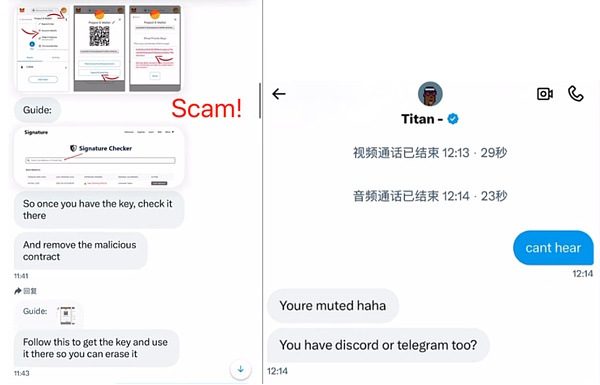
The scammers also provided so-called"operation tutorials" to guide users to paste their private keys into the input box of the phishing website, using the reason of "cancelling the interaction with the malicious contract" and even providing voice guidance services to urge users to take the bait in all aspects.
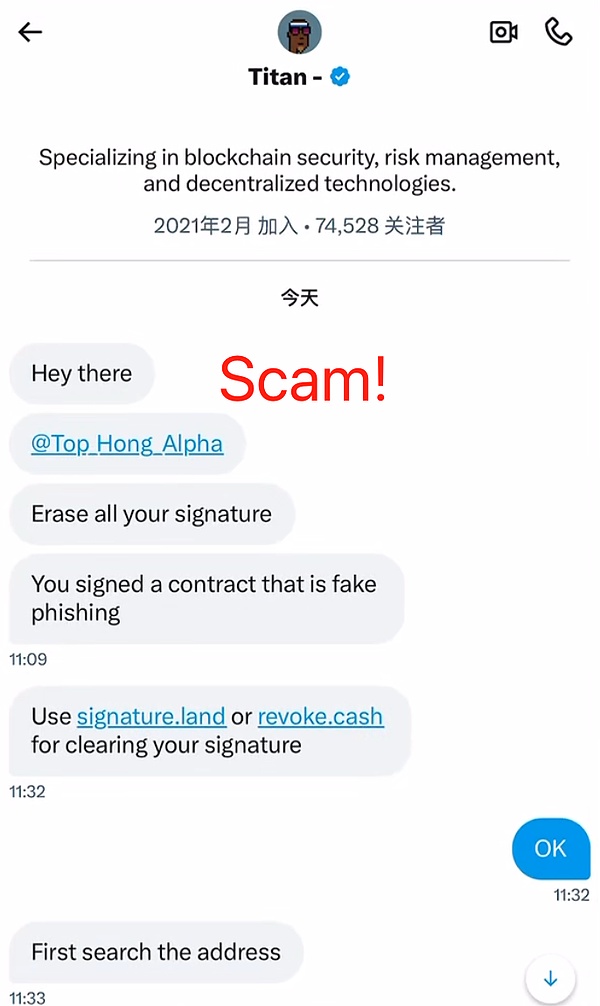
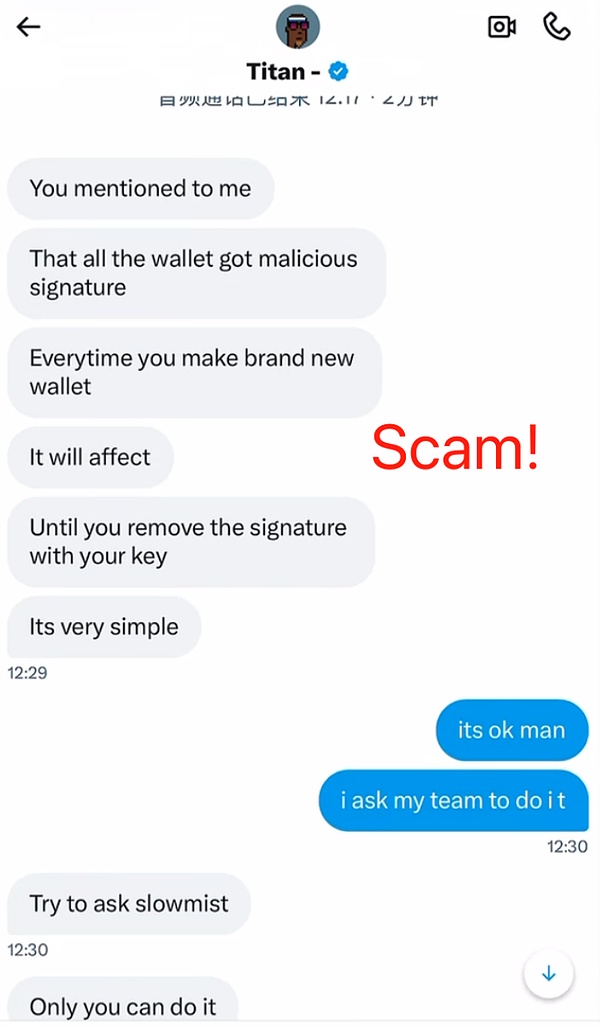
The user did not cooperate after noticing the abnormality, but the scammer did not give up. In order to further pressure and gain trust, the scammer suggested that the user consult the SlowMist security team. Some users who are not very vigilant may relax their vigilance and mistakenly think that the other party is not a scammer when they hear that the other party is willing to ask the security company to verify. The scammers often bet that the user will not really verify, and even directly@SlowMist_Team during the scam, trying to use the security company to endorse themselves.
Fortunately, the user was vigilant enough and did not enter the private key as instructed by the other party. Instead, he took the initiative to contact the SlowMist security team to verify the situation. It was finally confirmed that this was a scam, and the loss of assets was successfully avoided.
Multiple security expert identities
We further investigated and found that the scammer stole the avatar of the well-known on-chain detective ZachXBT on Telegram.
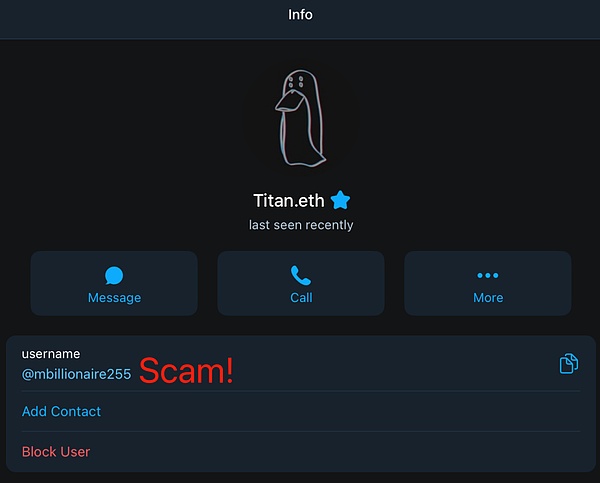
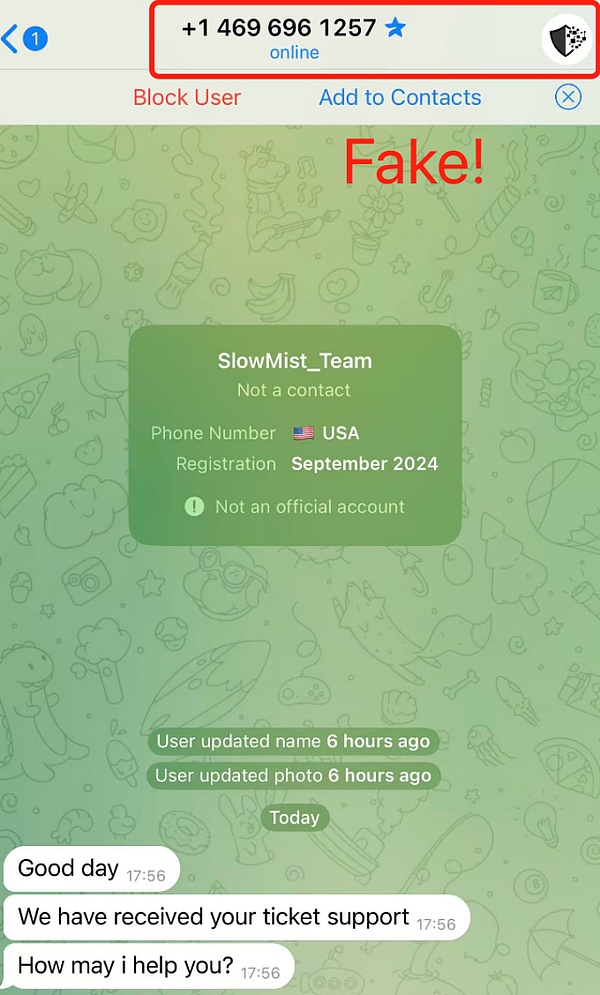
Since the user did not continue to cooperate, the scammer then pretended to be a SlowMist employee and continued to try to contact and defraud.
Check the scammer's X account (@Titanspace3), which has 74,000 followers and was registered in 2021, but did not become active until 2024. The account content mainly reposts security researchers, security companies and media dynamics, claiming to focus on the field of blockchain security, and is obviously a purchased account. This type of account trading is very common in the gray industry. We have previously analyzed related content, see True and false project parties | Beware of high-imitation phishing in the comment area.
Combined with the language style of his early tweets and the clues provided by users, it is speculated that the scammer may be from Indonesia.
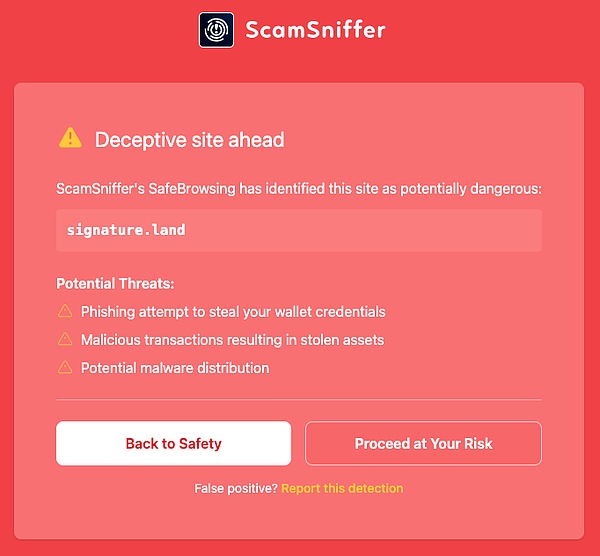
Currently, the account is still active on the X platform, constantly leaving messages in the name of "friendly reminders", guiding Web3 users to click on phishing links and inducing them to disclose private keys. The Web3 anti-fraud platform Scam Sniffer has marked the website as malicious.
Written at the end
From forging the "authorization risk" page to impersonating security company employees, step by step guiding users to disclose private keys, the methods of this type of scam are becoming more and more sophisticated. The scammers believe that as long as they package themselves professionally enough, most people will not go deep into the verification, but will be led by the "sense of urgency" they create.
In this regard, we especially remind the majority of users to be vigilant against those who use the banner of security to do illegal things. In the dark forest of blockchain, only by maintaining a zero-trust attitude and continuous verification awareness can we defend the last line of defense for asset security. No matter who the other party claims to be, no matter how urgent the other party claims the situation is, please remain calm, verify through official channels, and do not hand over private keys or mnemonics because of panic. The SlowMist Security Team will also continue to disclose such cases to help users identify risks, be vigilant, and jointly protect the bottom line of security in the Web3 world.
 Clement
Clement
 Clement
Clement Clement
Clement Davin
Davin Clement
Clement YouQuan
YouQuan Catherine
Catherine Joy
Joy Jasper
Jasper Jixu
Jixu Hui Xin
Hui Xin