Examples of projects addressing this problem include:
Penumbra, providing shielded DEX functionality
Aztec, implementing private smart contracts through cryptographic logic
ZK Passport, an optionally public ID card
These systems require:
Encrypted execution environment
Privacy-preserving messaging
Synchronization across private state machines
This often requires coordination among multiple parties, which is where MPC excels.
Privacy Solution Evaluation Framework
To cope with this complexity, privacy systems need to be evaluated from three dimensions:
Privacy Scope
Data Privacy: Hide transaction amounts, balances, or contract status
Identity Privacy: Hide participant relationships and addresses
Procedure Privacy: Encrypt contract logic and execution process
Metadata Privacy: Hide time, frequency, and interaction patterns
Programmability
Can developers build custom privacy-preserving applications?
Are there composable privacy primitives?
Can privacy policies be encoded and automatically enforced?
Is selective disclosure programmable and revocable?
Security Model
What trust assumptions exist? (hardware, committee, cryptography)
Is privacy opt-in or default?
Are these guarantees quantum-resistant?
How is privacy compromised when attacked or compromised?
As Vitalik Buterin said: "A chain is only as strong as its weakest trust assumption. Strong privacy means reducing those assumptions as much as possible."
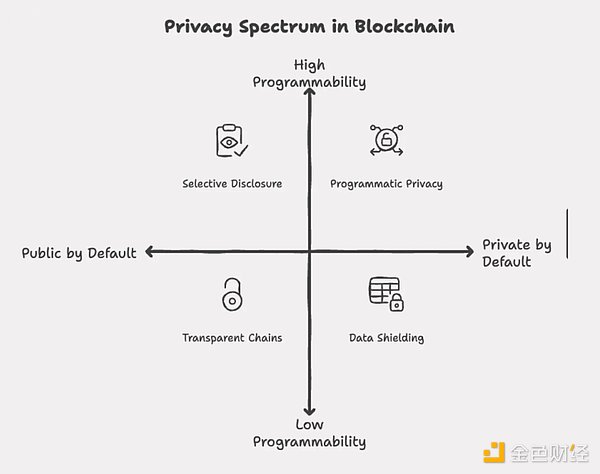
Privacy Design Space Beyond Payment
Currently, most of the research and development of privacy technology focuses on "currency", but the truly broad design space goes far beyond that, and also includes:
Games: Hidden state and fog of war logic
Governance: Coercion-resistant voting systems
Identity: On-chain reputation systems that do not require wallet addresses
Artificial Intelligence: Privacy-preserving inference computations for personalized agents
These systems require not only confidentiality, but also programmable, revocable, and composable privacy mechanisms.
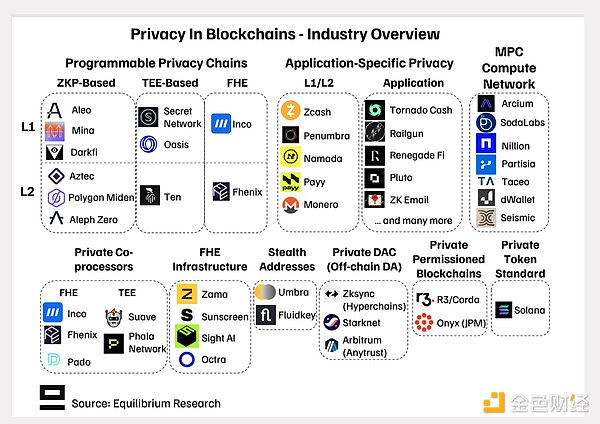
Leading Projects: Redefining the Privacy Landscape
Arcium
Arcium is a project focused on privacy-preserving decentralized computing, with MPC (Multi-Party Secure Computation) first as its design core. Its architecture separates key custody (implemented through N/N MPC) from high-performance computing (using rotating MPC committees), achieving scalability while maintaining cryptographic security.
Key innovations include: confidential AI model training, encrypted trading strategies, and DeFi order flow privacy protection. Arcium is also conducting research on forward privacy and quantum attack resistance to prepare for future infrastructure.
Aztec
Aztec is the next generation of privacy-focused Rollup, supporting fully encrypted smart contract execution through its self-developed Noir programming language and zkVM (zero-knowledge virtual machine). Unlike simple mixers, Aztec encrypts not only transaction data, but also the program logic itself.
Its "public-private hybrid" model allows applications to selectively share private state through cryptographic commitments, striking a balance between privacy and composability. The roadmap also includes: recursive proof technology and privacy-preserving cross-chain bridges.
Nillion
Nillion has built a new privacy infrastructure around a concept called blind computing - that is, computing can be done without revealing the content of the data and without a consensus mechanism.
Instead of implementing privacy directly on L1 or L2, Nillion provides a decentralized computing layer to assist existing blockchains and achieve confidential computing at scale.
Its architecture combines multiple privacy-enhancing technologies (PETs), including MPC, FHE (fully homomorphic encryption), TEE (trusted execution environment) and ZKP, and is coordinated through a network of nodes called Petnet. These nodes can process secret shared data without communicating with each other, thereby achieving fast, low-trust assumption privacy computing.
Core innovations include:
nilDB: a distributed private key-value database for querying and storing encrypted data
nilVM: a virtual machine for writing and executing blind computing logic, using a custom language Nada
nilAI: an AI privacy infrastructure that supports training and reasoning on encrypted data
Enterprise Node Clusters: a global node operator program with partners including Vodafone, Deutsche Telekom, Alibaba Cloud, etc.
Nillion Designed for developers who need encrypted logic, secure multi-party processes or private data analysis, it is suitable for fields such as medical, AI, identity recognition, and finance. Its goal is to become the "privacy layer of the Internet", providing programmable, composable, and scalable privacy capabilities.
Penumbra
As a sovereign Cosmos chain, Penumbra introduces privacy protection at the protocol level, rather than just implementing privacy functions at the application layer. Its Shielded DeFi module supports confidential trading, staking, and governance functions through multi-asset privacy pools.
Its innovative intention-driven trading system supports encrypted order flow matching, while protecting market privacy, allowing more complex financial interaction logic.
Zama
Zama is committed to applying fully homomorphic encryption (FHE) to blockchain scenarios and making it feasible in real-world environments. Through its TFHE encryption library and developer SDK, Zama enables the ability to perform calculations on encrypted data without decryption. Zama also combines FHE with MPC for key management to create a hybrid system that strikes a balance between security, performance, and usability, suitable for application scenarios such as private machine learning reasoning and confidential data analysis.
The way forward: programmable privacy
The future is not a choice between "transparency" and "privacy", but to achieve programmable privacy - allowing users and applications to set granular disclosure rules:
"Share these financial data only with verified auditors"
“Disclose this transaction record only if fraud can be mathematically proven”
“Allow this AI model to learn from my data, but do not store or share it”
To achieve this, privacy must become a “first-class citizen” in blockchain design, rather than an add-on feature spliced onto a transparent system later.
Conclusion: Think of Privacy as Digital Infrastructure
Privacy is not an add-on feature for a few extreme scenarios or illegal activities. It is the foundation of digital sovereignty and the premise for blockchain to truly meet human needs rather than serve “surveillance capitalism”.
We are at a critical inflection point: the encryption tools already exist. Economic incentives are aligning. The regulatory landscape is evolving. What’s really needed now is a shift in consciousness: privacy isn’t about hiding, it’s about choosing.
Blockchains give users self-custody of their assets, while privacy-enhancing technologies (PETs) will give users self-custody of their information, relationships, and identities. It’s the difference between “controlling your private keys” and “controlling your entire digital life.”
The question isn’t whether privacy will come to the blockchain world, but whether it will come through user demand or through regulatory coercion. Projects building privacy infrastructure today are preparing for both possibilities.
Privacy is sovereignty. Privacy is choice. Privacy is the future of human-centric technology.
 Weatherly
Weatherly

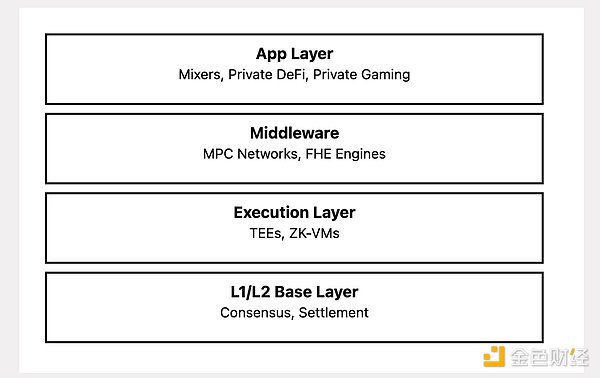
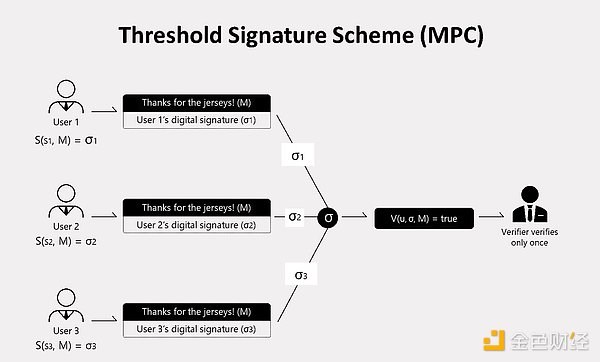
 MPC allows multiple parties to jointly compute on encrypted data without revealing the inputs. It is useful for both:
MPC allows multiple parties to jointly compute on encrypted data without revealing the inputs. It is useful for both:




