Deng Tong, Jinse Finance
In 2025, the cryptocurrency industry saw increasingly clear regulations, deeper penetration by traditional finance, and accelerated technological iteration. Each key juncture was inseparable from key figures who either guided policy direction, led institutional entry, tackled technical challenges, or stirred up the market.
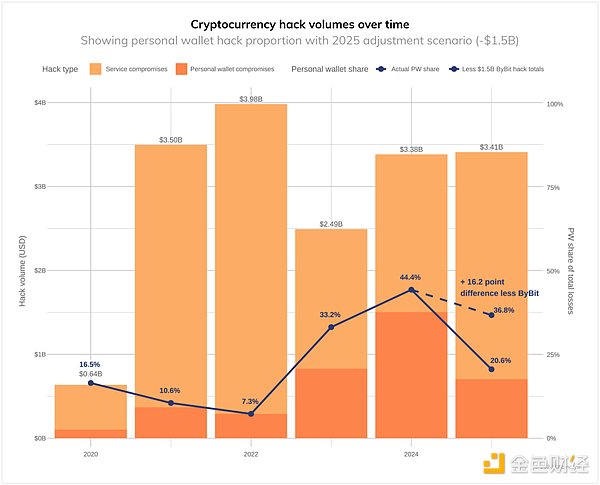
According to Chainalysis data, from January to early December 2025, the cryptocurrency industry suffered over $3.4 billion in thefts, with the Bybit theft in February alone causing $1.5 billion in losses.
This article reviews the crypto industry hacking incidents of 2025.
I. Bybit: $1.46 Billion
On February 21, Dubai-based cryptocurrency exchange Bybit suffered a theft of approximately $1.46 billion in crypto assets. Preliminary reports indicate that attackers used malware to trick the exchange into approving transactions that transferred funds to the thieves' accounts. This is the largest cryptocurrency theft to date, far exceeding the $611 million stolen from Poly Network in 2021.
The North Korean organization Lazarus Group is believed to be the mastermind behind this theft.
According to an official announcement from Bybit, hackers successfully controlled an Ethereum cold wallet and dispersed 401,000 crypto assets to 48 anonymous addresses by using a phishing website impersonating a multi-signature wallet service provider to induce internal signers to authorize transfers. Some of the assets were even converted to Bitcoin via cross-chain bridges to cover their tracks. Ethereum prices fell 4% in a single day, and Bitcoin was also dragged down by sentiment, fluctuating downwards from a high of $105,000, briefly falling below the $90,000 mark. For details, please see the Jinse Finance special report
"The Nightmare Weekend of Bybit's Biggest Theft in History"II. Cetus: $260 Million
On May 22, Cetus suffered a complex smart contract attack targeting the CLMM pool. The attackers discovered a vulnerability in the contract and, by constructing transactions, stole assets in multiple rounds of operations.
This attack did not stem from security flaws in the Sui underlying public chain or the Move language. The core issue lies in the design of Cetus's own open-source codebase, serving as a wake-up call for code auditing of decentralized projects across the industry. For details, please see
"After the Cetus Hacking: What Should We Learn from This Incident?"III. Balancer: $128 Million
On November 3rd, the DeFi protocol Balancer was hacked, resulting in the theft of over $100 million in digital assets. The core losses were concentrated in the USDe pools on the Berachain chain, with stolen assets valued at approximately $128 million, making it one of the major security incidents in the DeFi field in 2025.
This attack stemmed from a design flaw in Balancer V2 Composable Stable Pools (CSP). It only affected CSPv5 pools whose pause windows had already expired; CSPv6 pools were unaffected because they were automatically paused by Hypernative. Other V2 pool types and the V3 architecture remained secure. The Balancer theft, coupled with selling pressure from the nearly $100 million stolen assets, caused SOL's 24-hour drop to nearly 10%. Prior to this, Balancer had undergone 11 audits. For details, please see
"5 Years, 11 Audits, 6 Thefts: Why Does Balancer Still Have Fans Despite Its Long History of Scandals"IV. Nobitex: $81.7 Million
On June 18th, blockchain detective ZachXBT revealed that Nobitex, Iran's largest cryptocurrency exchange, was suspected of being hacked, involving the abnormal transfer of large sums of assets across multiple public chains. The affected assets included TRON, EVM, and BTC networks, with preliminary estimates of losses at approximately $81.7 million. The attackers not only transferred funds but also actively transferred a large amount of assets to a specially designed destruction address; the "burned" assets were worth nearly $100 million.
The hacker group Predatory Sparrow (Gonjeshke Darande) claimed responsibility for the attack and announced that it would release Nobitex's source code and internal data within 24 hours.
For details, please see
"Nearly $100 Million Destroyed: A Review of the Nobitex Theft Incident in Iran"V. UPCX: $70 Million
On April 1st, the crypto payment protocol UPCX suffered a serious privilege theft attack. Attackers successfully hijacked the platform's core administrator privileges and transferred approximately $70 million worth of crypto assets by freezing liquidity pools and modifying trading parameters.
Security agencies' review shows that the core breakthrough of this attack lies in the fatal flaw in UPCX's permission management system: the platform did not use a multi-signature mechanism to constrain administrator privileges, allowing a single core account to complete high-risk operations such as freezing liquidity and transferring assets. Furthermore, the login authentication mechanism for this account was too simple, relying only on account password + SMS verification, without introducing enhanced protection measures such as hardware wallets and two-factor authentication.
Attackers successfully obtained administrator account information through a combination of social engineering database cracking and phishing emails. After logging in, they quickly executed malicious operations: first, they froze the main liquidity pools within the UPCX ecosystem, preventing users from trading and withdrawing funds normally; then, they modified asset transfer rules, transferring core assets in batches to anonymous addresses under their control; finally, they deleted some operation logs in an attempt to cover up the attack. VI. CoinDCX: $44.2 Million CoinDCX Data Breach Incident: In July 2025, the Indian cryptocurrency exchange CoinDCX suffered a server intrusion, and its internal operating accounts were attacked. This attack resulted in a loss of $44.2 million. CoinDCX absorbed all the losses to protect user funds, setting a benchmark for transparency and user trust. The core reason for this incident was that an employee "took on a side job" and leaked management privileges, which were then exploited by internal personnel in collusion with external hackers. This is a typical case of "insider + external hacker" collusion attack, highlighting the importance of internal personnel management in exchanges.
VII. GMX: $42 Million
On July 9th, the decentralized derivatives protocol GMX suffered a management vulnerability attack, resulting in a loss of approximately $42 million. The unique aspect of this incident is that the vulnerability was not natively present, but rather a new logical flaw introduced by the platform team while fixing an old vulnerability. This flaw was exploited by hackers, creating an embarrassing situation of "the more you fix, the more leaky it becomes."
The root cause lies in an incorrect call to the `executeDecreaseOrder` function: the first parameter of this function should have been an External Account (EOA), but the attacker passed in a smart contract address. This allowed the attacker to manipulate the internal state during the redemption process, ultimately extracting assets worth far exceeding the actual value of their GLP holdings.
In the aftermath, the GMX team immediately suspended all trading functions of the V2 version contract, issued an emergency announcement acknowledging the new flaw introduced while fixing the vulnerability, and launched a user compensation plan, fully compensating affected users through the platform's insurance fund.
For details, please see "Detailed Explanation of the $40 Million GMX Vulnerability Attack"
VIII. x402bridge: $38 Million
On October 28th, the cross-chain bridge protocol x402bridge suffered an asset theft incident, with losses amounting to approximately $38 million. The core reason for this attack was the theft of the administrator's private key due to improper storage on the server, resulting in the large-scale transfer of cross-chain assets.
To improve the efficiency of cross-chain transactions, the x402bridge administrator stored the core private key in shards across multiple cloud servers, but did not perform sufficient security hardening on the servers, only adopting basic firewall protection, and the encryption strength of the private key shards was low.
For details, please see
"A Review of the 402Bridge Attack: What Other Cases of Theft Due to Private Key Leaks"IX. Upbit: $36 Million
On November 27, Upbit disclosed that it suffered a 54 billion won ($36 million) attack on the Solana network, and Upbit will bear all customer losses. Some Solana network assets (worth approximately 54 billion won) were transferred to an unknown external wallet. After detecting the abnormal withdrawal, Upbit immediately conducted an emergency security review of the relevant network and wallet system.
For details, please see
"Upbit Hacked: Industry Changes Under Naver's $10.3 Billion Acquisition"X. UXLINK: $11.3 Million
On September 23, UXLINK was attacked due to the leakage of its multi-signature wallet private key. The attacker minted UXLINK tokens and sold them, profiting over $11.3 million.
Due to the leakage of the UXLINK project contract's private key, the attacker's address was added to its contract's multi-signature account, and other original multi-signature accounts were removed. Furthermore, the contract's signature threshold was reset to 1, meaning that only the attacker's address needed to sign to execute contract operations. The attacker achieved complete control over the contract. Subsequently, the attacker began issuing more UXLINK tokens and selling them for profit.
For details, please see
"Over Ten Million Dollars Loss: UXLINK Security Incident Vulnerability Analysis and Stolen Funds Tracking"Appendix: How Much Money Did North Korea Steal in 2025?
According to Chainalysis data: In 2025, North Korean hackers stole at least $2.02 billion in cryptocurrency (an increase of $681 million from 2024), a year-on-year increase of 51%. In terms of the amount stolen, this was the worst year for North Korean cryptocurrency thefts on record, and North Korean attacks accounted for 76% of all service intrusions, setting a new record. Overall, the 2025 data brings the minimum estimated total amount of cryptocurrency funds stolen by North Korea to $6.75 billion.
North Korea typically infiltrates IT personnel into crypto services to gain privileged access and carry out high-impact attacks.
This year's record number of attacks may indicate that North Korea is increasingly reliant on IT personnel to infiltrate exchanges, hosting firms, and Web3 companies, which can accelerate initial access and prepare for large-scale theft. North Korean hackers are no longer simply applying for jobs and infiltrating companies; they are increasingly impersonating recruiters from well-known Web3 and AI companies, meticulously crafting fake recruitment processes, and ultimately stealing victims' credentials, source code, and VPN or SSO access under the guise of "technical screening." At the corporate executive level, similar social engineering tactics are emerging, posing as strategic investors or acquirers, probing for sensitive system information and potential high-value infrastructure access paths through presentations and fake due diligence—an evolution directly built on North Korea's fraudulent activities targeting IT professionals and its focus on strategically important AI and blockchain companies. The prominent North Korean hacking group, Lazarus Group, is allegedly operated by the North Korean government. While little is known about the group, researchers have attributed numerous cyberattacks launched since 2010 to it. According to defector Kim Kuk-song, this unit is known internally in North Korea as the "414 Liaison Office." The group's earliest known attack, known as "Operation Trojan," occurred between 2009 and 2012. This was a cyber espionage campaign that used simple distributed denial-of-service (DDoS) attacks against the South Korean government in Seoul. They also launched attacks in 2011 and 2013. While not definitively proven, they may also be behind the 2007 attacks against South Korea. How could a country where most people have no internet access cultivate so many highly skilled hackers? Thae Yong-ho, the former Pyongyang ambassador to London who defected to South Korea in 2016, pointed out that Kim Jong-un spent most of his time playing video games while studying in Switzerland, but he also saw the importance of computers in modern life. Therefore, after returning to South Korea with his brother Kim Jong-chol, he inspired their father. "Kim Jong-il quickly realized the advantages of these computers and networks." Kim Jong-il quickly established specialized schools to teach high-tech espionage, intelligence, and warfare. Five years later, the rewards were substantial: the hackers stole top-secret South Korean military plans, including documents outlining a potential war between North Korea and its northern neighbor, and a plot to "decapitate" North Korea by assassinating Kim Jong-un. North Korea's cyber force is now believed to number over 8,000, most of whom are handpicked math prodigies from schools. In North Korea, they belong to a seemingly harmless "Reconnaissance General Bureau," but in practice, their cyber codenames include Lazarus, BeagleBoyz, Hidden Cobra, and APT38 ("APT" stands for "Advanced Persistent Threat"). These students undergo intensive, long-term training, but they also receive certain privileges—including exemption from state-run labor programs, material benefits such as cars and comfortable housing, and rare opportunities for international travel, such as participating in global math competitions like the International Mathematical Olympiad. North Korea's money laundering activities exhibit a unique pattern, with over 60% of transactions concentrated in transfers under $500,000. North Korean hackers tend to favor: Chinese-language money transfer and escrow services (up 355% to over 1000%): This is their most prominent characteristic, indicating a heavy reliance on Chinese-language escrow services and a money laundering network comprised of numerous operators with potentially weaker compliance controls. Bridging services (up to 97%): A heavy reliance on cross-chain bridges to transfer assets between blockchains, attempting to increase the difficulty of tracing. Hybrid services (up 100%): Increased use of hybrid services to attempt to conceal money transfers. Specialized services like Huione (+356%): Strategically utilizing specific services to facilitate their money laundering activities.
Note: Huione is a financial group headquartered in Phnom Penh, Cambodia. Its core businesses include payments, guarantees, and cryptocurrency trading. Since July 2024, it has been accused by multiple countries of money laundering and related online fraud fund transfers. In November, it was sanctioned by the US Treasury Department, and in December, the National Bank of Cambodia suspended some of its operations.
For details, please see "Unveiling the Shocking Cryptographic Case Carried Out by North Korean Hackers: Why Was It So Powerful? Where Did the Money Go?"
 Anais
Anais





